IoT is a very popular term these days. It stands for the Internet of Things. According to Oracle, the IoT is an umbrella term. It gathers all smart devices used by people and businesses. In most cases, the devices have sensors and microchips. Also, they are connected to other devices or the Internet. For example, smart gas leak sensors, a wireless doorbell camera, or robotic vacuum cleaners are the components of IoT.
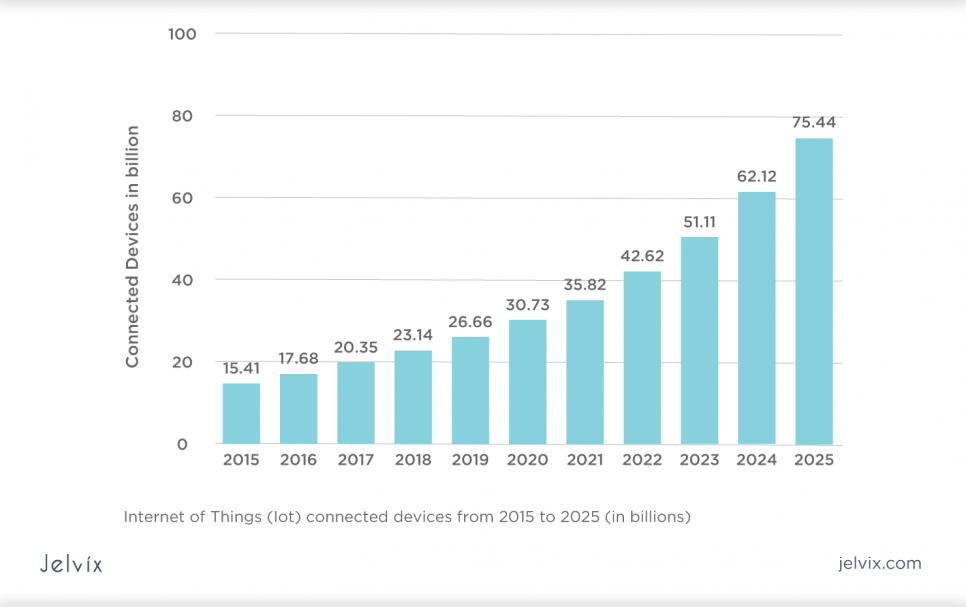
The market has exploded recently, and it’s not going to slow down the pace of development. According to ResearchGate, more than 75 billion IoT devices will be connected to the Internet by 2025.
All devices connected to the Internet need a unique IP address. But, the massive adoption of IoT components forced a shortage o IPv4 addresses. Consequently, the IPv6 protocol has become massively used recently.
What Is IoT Architecture?
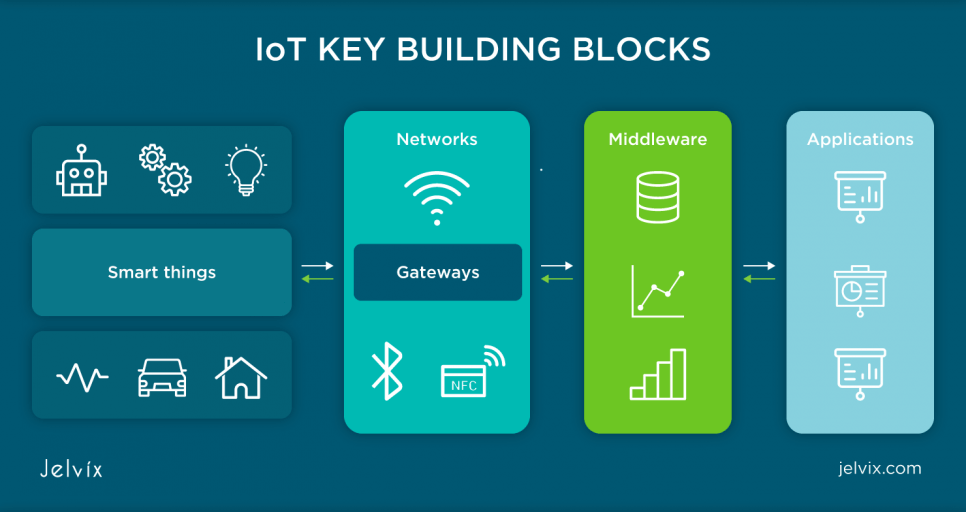
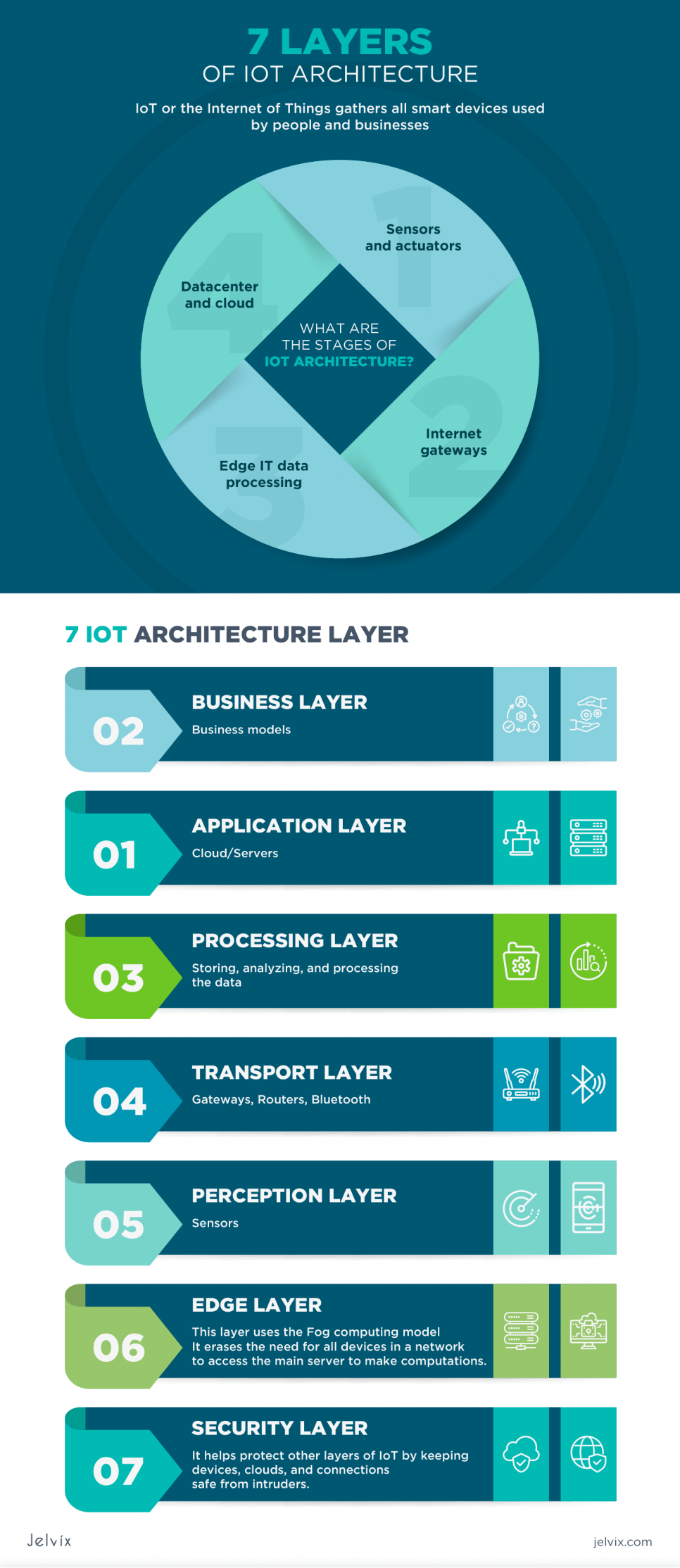
IoT devices are not helpful when they are utilized separately. Smart sensors connected to the Internet bring an advantage to businesses. A well-developed architecture of IoT devices foresees the ability to create automated systems. They help run large mechanisms hassle-free. What are the stages of IoT architecture? In a nutshell, an IoT architecture comprises four crucial stages. They are the following:
- Sensors and actuators.
- Internet gateways.
- Edge IT data processing.
- Datacenter and cloud.
IoT devices have to be integrated into a complicated system to gather data, analyze it, and send commands. Such a system implies a lot of IoT architecture layers. Do you want to discover what the Internet of Things architecture layers are in more detail?
If so, you’re at the right place. Below, you will be able to dive deeper into the architecture of IoT.
Crucial Thing To Know About IoT Architecture
There is one thing you have to remember about the IoT architecture before taking a deeper dive into the topic. Note, there is no one-size-fits-all solution that works for all projects. The complexity of an IoT ecosystem used by a business depends on the tasks connected devices need to tackle. Therefore, it’s vital to know about all the IoT architecture layers to create a system that meets all the requirements.
Nevertheless, even though almost every IoT system deployment is unique, its architecture is limited by particular layers. Keep reading the post to learn more about the Internet of Things architecture layers that can be used.
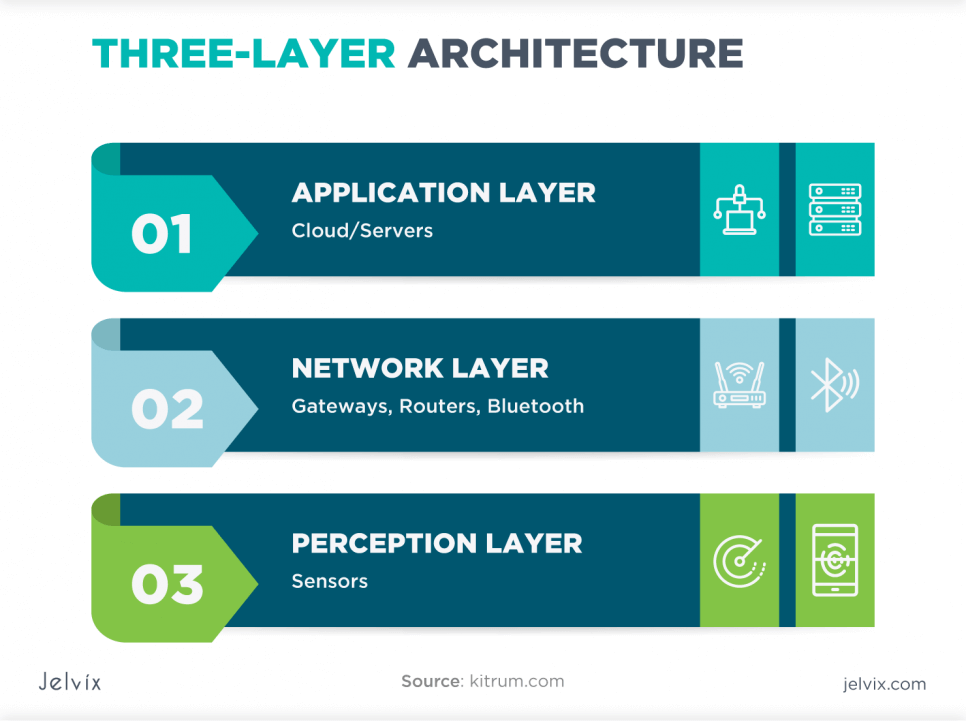
Three-Layer Architecture
The basic IoT layered architecture was widely used at the dawn of IoT technology development. The three-layered architecture can still be utilized because it is easy to implement. However, it has a lot of drawbacks. Many security threats are the most important reason why this architecture is almost not used these days.
Perception Layer
It is the foremost layer that is also known as the sensor layer. It implies all types of sensors that can be used in IoT devices. They gauge particular parameters. Then, they transform signals from the environment sensors interact with them into digital information. Sensors can help create smart premises maintenance systems. The most popular ones that represent the first IoT architecture layer are temperature, pressure, and infrared sensors.
- Temperature sensors: This type of sensor is used in almost any industry. They help control the temperature of water in household heating systems. Also, they are used in refrigerators, computers, and vehicles.
- Humidity sensors: They are widely used in HVAC systems. Besides, humidity sensors are crucial for industrial premises. It’s vital to maintain the required humidity level to produce certain quality products.
- Pressure sensors: With the help of this type of sensor, people can measure the flow of air or liquids. They are used in tech development.
- Level sensors: They can be found in almost any car, refrigerator, or household. Level sensors gauge the number of liquids in tanks or gas in the air.
- Infrared sensors: This type of sensor can detect motion. Infrared sensors are mainly used for security purposes. Also, they help lower the usage of electricity.
Widespread Security Threats
The Perception layer implies devices that collect information and receive commands from users. It is one of the most sensitive IoT architecture layers. As a result, scammers conduct a lot of different attacks to get control over them and access the data they gather. Down below, you will find the most popular threats of this layer.
- Eavesdropping. A lot of IoT devices help people to communicate with each other. A wireless doorbell camera or a smart speaker is the most popular. However, if a device is vulnerable, there is a high chance that a hacker will attack it to access people’s personal conversations.
- Node capture. This type of attack aims to steal the data stored on IoT devices. To achieve the goal, attackers gain access to a crucial node that helps access the memory of a device.
- Timing attack. It is a complicated type of attack that needs attackers to analyze the time required by IoT devices to respond. If devices have low computing power and take a lot of time to respond, hackers can find vulnerabilities to utilize.
Network Layer
It is known as a gateway layer that helps establish the logical design of IoT by connecting devices with a platform. The data captured by sensors get transmitted by wires or radio to back-end IoT services. The transferred data is secured to prevent unauthorized access. In most cases, the transmitted information is encrypted. The most popular IoT communication models are the following:
- Ethernet: It is a secure way to connect IoT devices using a wire. It makes the connection reliable and secure. However, good wire management is required to connect many IoT components using Ethernet.
- WiFi: A wireless network is one of the most convenient ways to connect IoT devices. It erases the need to use wires, which works well in small premises. However, WiFi routers have limited signal ranges, making it hard to connect all components of IoT in large premises using WiFi.
- NFC (Near Field Communication): NFC is a technology that ensures fast and hassle-free data transfer between two IoT devices. It is rarely used because it needs two devices to be placed in 3 inches or less. Moreover, the data transfer speed is low.
- Bluetooth: This technology helps transfer data, consuming low amounts of power. Therefore, it’s widely used by IoT devices powered by batteries. Unfortunately, on average, Bluetooth has a short-range signal that makes 30 feet.
When all devices are networked, a messaging protocol has to be configured. According to IBM, messaging protocols are rules that different devices and computers follow to understand the information and commands they exchange. The most popular protocols used in the second layer of the three layers of IoT architecture are the following:
- DDS (Data Distribution Service);
- AMQP (Advanced Message Queuing Protocol);
- CoAP (Constrained Application Protocol);
- MQTT (Message Queue Telemetry Transport).
Widespread Security Threats
The network layers are the most important in the Internet of Things architecture because it connects users with devices. So, many hackers attack this layer. They strive to get unauthorized access to IoT systems and manipulate them without permission. Here are the three most popular types of attacks.
- Man-in-The-Middle (MiTM) Attack. It is a severe attack on an IoT reference architecture because it allows hackers to manipulate devices in real-time. When this type of attack is conducted, a hacker intercepts requests between a sender and receiver and updates them.
- Storage Attack. Most IoT systems store the data collected from the devices’ sensors. The data is stored on hard drives in devices or clouds. Hackers frequently attack storage to download the gathered data.
- Exploit Attack. It is a type of attack that needs scammers to analyze particular IoT communication models. After doing it, they find loopholes and utilize them for unauthorized access to IoT systems.
Application Layer
What is the application layer in IoT architecture? It is the final layer in this IoT reference model. It represents all devices that use the IoT devices or systems deployed. It can be smart devices that help keep your houses clean and safe or entire smart-home systems that can be managed with the help of a smartphone. At the application layer, end-users interact with all the connected devices.
Widespread Security Threats
The layer has a lot of different issues that need to be resolved. However, security concerns are the most important ones. There are many different ways to attack devices in this layer to get unauthorized access. The most popular ones are the following:
- Cross-site scripting. Most websites that help interact with IoT devices are secure. Nevertheless, some of them have loopholes that hackers utilize. To access users’ sensitive data or get control over IoT devices, they insert a piece of code and run it as site administrators.
- Malicious code attack. All applications are vulnerable to malicious code attacks. Therefore, computer viruses spread all over the Internet can easily harm particular IoT devices or even ruin a complicated IoT model.
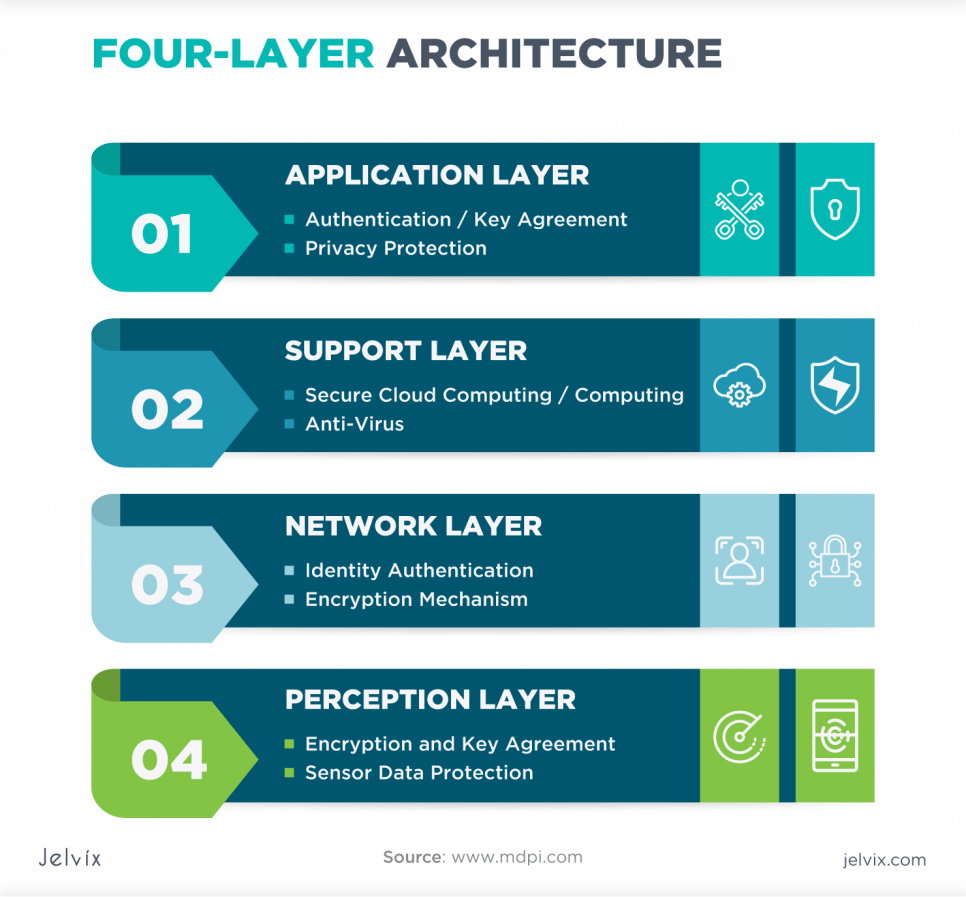
Four-Layer IoT Architecture
What are the 4 layers of IoT architecture? The architecture that uses four layers of IoT is similar to the basic one. The data is also collected by sensors and transferred to the storage system by the Network layer. However, this IoT reference architecture has one additional layer recognized as the Support layer. It helps resolve the main problem of the basic IoT architecture, which is weak security. The Support layer is placed between the Network and Perception layers.
Support Layer
There are a lot of threats that the three-layer logical design of IoT experienced. Therefore, it was offered to add another level that could resolve most issues. It’s also known as Secure because it focuses on making IoT communication models more protected from possible threats.
The support layer verifies if the information is sent from an authenticated user. In most cases, passwords or shared keys are used as authentication methods. After verifying a user, the Support layer sends information obtained from sensors of IoT devices to the Network layer. It is third in this IoT layered architecture.
Widespread Security Threats
The Support layer helps enhance security. However, it doesn’t protect all IoT architecture layers from all other threats. Since these attacks are very hard to conduct, the Support layer significantly enhances the security of an IoT reference model. The two most common threats are the following:
- DoS (Denial of Service) attack. In a nutshell, it needs a hacker to send a lot of requests to the network layer, so it won’t be able to process all of them simultaneously. In such a case, an overloaded system will stop working.
- Insider Attack. To conduct it, a scammer needs to get the login credentials of an existing IoT system user. After doing it, they can upload malicious code to the system to ruin it or get sensitive information.
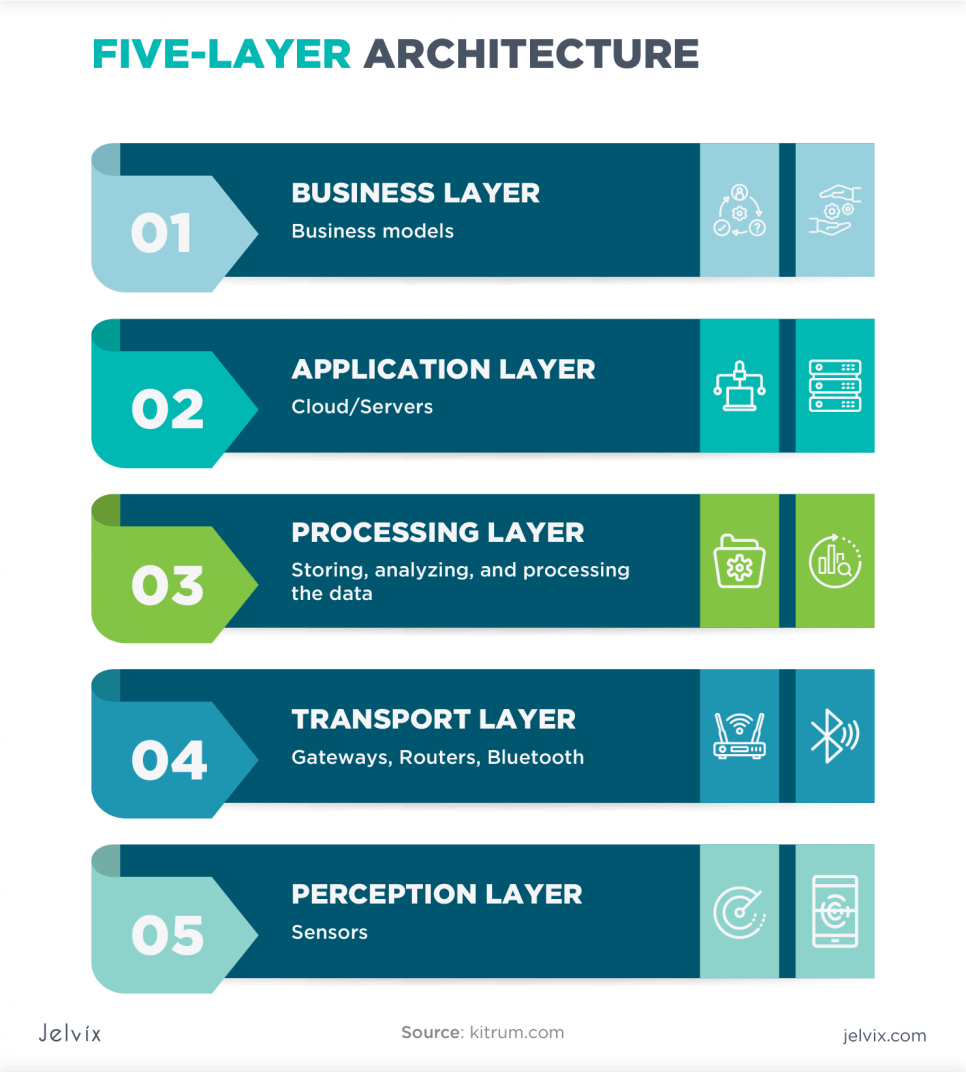
Five-Layer IoT Architecture
The model that implies four IoT architecture layers was a good solution. It helped enhance the security of the logical design of IoT. However, it wasn’t ideal. The architecture didn’t meet all the demands of users. Also, there were some security concerns. Therefore, the five-layer architecture has been developed.
But, this architecture isn’t an enhanced version of the four-layer iteration. Instead, this one consists of the basic architecture that implies two extra Internet of Things architecture layers. The two new layers are Processing and Business.
Processing Layer
It is a layer that gathers all the data provided by the perception layers through a network. All the information is stored and analyzed. It is one of the most important layers of IoT because it makes decisions based on data analysis. Also, the application layer interacts with a user to manage and operate their IoT devices. This layer is placed between Network and Application layers in the logical design of IoT architecture.
There are two major data processing stages of this layer.
- Data accumulation. All the data gathered by sensors of IoT devices don’t need to be used simultaneously. Therefore, it gets saved on devices’ hard drives or transferred to data lakes or different types of databases for further use and analysis. The main goal followed is to sort the gathered data to store it efficiently.
- Data abstraction. The gathered data is used for getting helpful insights at this stage. Usually, it’s supplemented with data provided by non-IoT devices to get helpful insights. At this stage, data gets unified or reconciled to particular formats. Finally, it gets gathered in one place to make it easy to access for users from different locations.
Widespread Security Threats
By adding a new layer that stores the gathered data securely, developers increased the security of the basic architecture of the Internet of Things. However, it doesn’t bring 100% security to a system. The most popular threats are the following:
- Malware. Since this layer gathers tons of data, there is a chance that trojans or computer viruses will get into a system. In addition, they may provide unauthorized access to data lakes and databases for scammers.
- Exhaustion. Another attack like DoS can cause it. This type of attack aims to drain the battery of a device or take 100% of a computers’ processing power and memory, so it won’t be able to tackle other tasks.
Business Layer
All IoT communication models strive to deliver convenience in information consumption to end-users. It is the top layer that is located above the Application layer. The Business layer ensures that users can use IoT systems hassle-free. For example, it takes raw data and forms insights in graphs and charts. This layer is related to decision-making because it interacts with stakeholders.
Widespread Security Threats
This layer is considered secure. Therefore, there are no serious threats to this IoT layered architecture. The only one that users should be aware of is the logic attack. It needs hackers to find any flaws in code conducted by developers and use them to get unauthorized access to important data. Also, there is always a chance that this layer may have zero-day vulnerability.
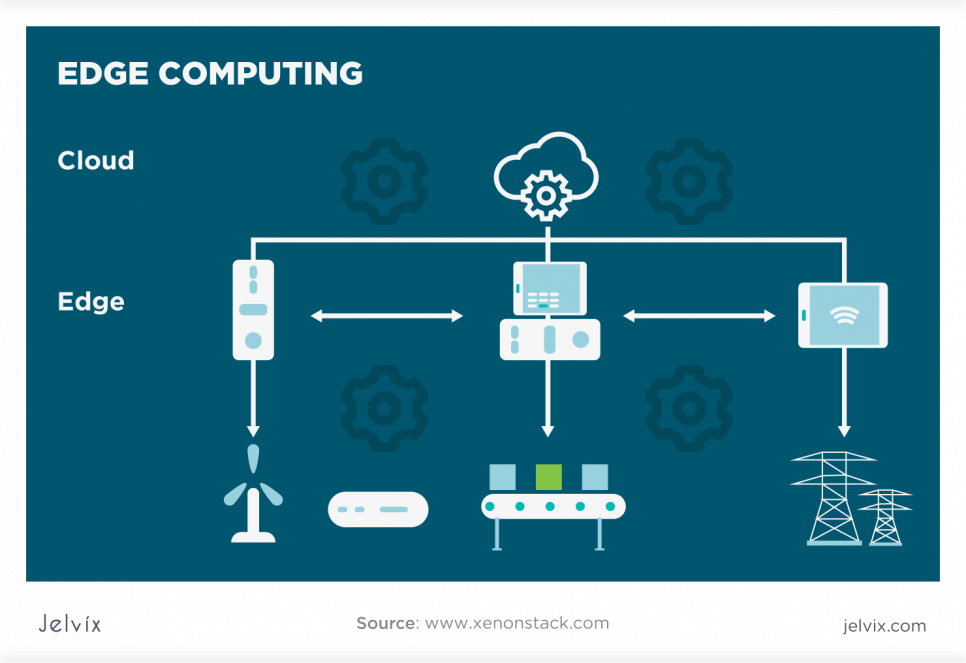
Edge Layer – Additional IoT Architecture Layer
An additional layer may enhance the architecture that implies five IoT architecture layers. The demand in this layer has appeared because the amount of data processed by IoT devices has increased significantly. Moreover, it helps build a large-scale IoT reference model. The layer is placed between the Network and Processing layers.
This layer uses the Fog computing model, which enhances large-scale IoT systems. It erases the need for all devices in a network to access the main server to make computations. Instead, most computations are made on devices locally. Also, it helps decrease the data storage and transferring because most information is stored locally on devices.
Security Layer – Important Component of IoT Architecture
Additional layers increase security compared to the basic IoT reference architecture. Nevertheless, there are a lot of different threats that IoT devices and systems experience. Therefore, additional layers have been developed to protect sensitive data and IoT deployments.
The Security layer is considered the seventh. Thus, now you know the answer to the question, “What are the seven layers of IoT?” It helps protect other layers of IoT by keeping devices, clouds, and connections safe from intruders.
Wapping Up
The IoT market develops at a high pace these days. The number of smart devices connected to the Internet grows exponentially year by year. Since most people use IoT devices constantly and share large amounts of sensitive data, the IoT architecture has added four additional layers.
There were only three vital IoT architecture layers when the technology was developed. However, some systems use from five to seven Internet of Things architecture layers these days. Thanks to Jelvix’s extensive expertise in IoT, our specialists can build a system of any complexity.
Feel free to contact us if you want to create a forward-looking IoT solution that will help you reduce spending, automate processes, and enhance supply chains.