Gone are the days when tangible assets represented the bulk of the value of an organization. Now, an important resource and a key factor in economic success and business value creation is intellectual capital, which is estimated to account for 90% of the total value of modern companies.
This intangible asset includes organizational processes, employee experience, the body of knowledge, and resources available in the organization. It can attract new customers, create new products, increase profits, or any other business improvement.
That makes sense – your ability to innovate and develop best-in-class technology makes you a market leader and enables you to attract esteemed clients. But defending your intellectual property, whether it is confidential information or inventions under development, will keep you competitive.
What Is Intellectual Property And How Is It Protected?
According to Investopedia’s definition, intellectual property (IP) is a set of intangible assets owned by a company and legally protected from being sold without consent or external use. The value of intellectual property lies in your exclusive right to manufacture, use, reproduce, or promote a unique creation or idea as an asset to your company.
The concept of IP implies that certain products of human intelligence should be as protected as a physical property called tangible assets. Since the creation of IP requires many hours of skilled labor and investment in intellectual resources, these investments must be protected.
For this, most developed countries have developed legal mechanisms to protect both forms of ownership. They outline all the steps preventing the usage of your idea or product and making a profit from it without your permission. Thus, the intellectual property right is your privilege to the result of your intellectual activity or another object of IP determined by law.
Peculiarities Of Intellectual Property Protection
The IT industry generates innovation almost all the time. But to maintain control over their innovative products, companies must use the protections provided by law. Without this protection, innovators will not be able to decide for themselves whether their code will be “open,” licensed, or not available to the public. Moreover, there is a possibility that creators could lose the right to their idea without resorting to legal remedies.
How intellectual property is protected depends mainly on its nature, and it is not always easy to determine the best one. For example, some IP assets require only one type of protection, while others require two or more. Another factor that organizations should consider before deciding on their IP protection strategy is the cost. Applying for a patent is a complex and costly process that can be overwhelming for small tech companies on a tight budget.
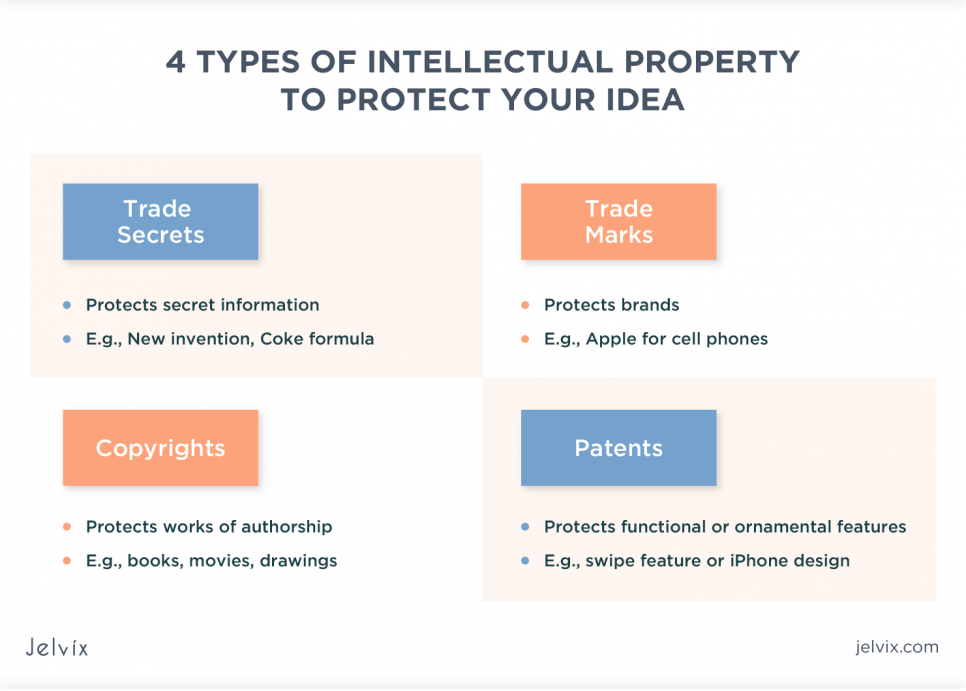
There are four main ways:
- Copyrights;
- Patents;
- Trademarks;
- Trade secrets.
Let’s see how these types of intellectual property apply to IT products.
Copyright
This type of protection is provided automatically when creating a copyright product such as writing the source code, creating a user interface, or compiling a program. However, if you want to protect copyright from someone infringing on your work, you must obtain a registration certificate for the copyrighted work.
Copyright protection is granted for all source code whether it is a trade secret, released as object code, or “open source.” The copyright application process allows copyright holders to designate even portions of the source code as trade secrets.
It should be noted that copyright protects the display of an idea, not the idea itself. Therefore, only the program is protected, not its functionality. If you want to preserve the functionality of the software, apply for patent protection.
Patent
In IT, computer processes are usually patented. For example, in the United States, the software can be protected if unique and tied to a machine. However, for software to be patentable, it must offer some measurable improvement.
For example, a simple implementation of something that can be done on a computer (such as multiplication of numbers) or “abstract idea” cannot be patented. Therefore, in IT, patents are most often used to protect proprietary algorithms or software architectures.
In Europe, “computer programs” are excluded from patentability. The EPO considers a program to be non-patentable if it cannot cause an “additional technical effect” that goes beyond the internal technical interaction between hardware and software. While the source code may not be proprietary, this does not mean that you cannot patent the invention of software. It can be considered patentable if it offers a technical solution to a specific problem.
A patent protects an invention, technical product, or process from illegal use, resale, lease, or transfer to third parties. And, accordingly, it offers much broader protection than copyright. The patentee can grant a patent license to use the patented subject matter for a fee.
Trademark
As USPTO defines, a trademark is “a symbol, word, phrase, pattern, or combination of all the above that identifies the origin of goods on one side from those on the other. For example, a company name, logo, or slogan can be registered as a trademark and become a brand identifier for your business or products.
Words, phrases, and images are usually the most common intellectual property subject to trademark registration. However, you may register any other distinctive feature for your company. These business assets also need to be protected because they prevent competitors from using the brand’s reputation over the years. To avoid intellectual property rights violations, a trademark must be registered.
Trade secret
It is a comprehensive concept covering everything from a new, more efficient business to unique architecture applications. A trade secret can even be considered a non-public company process or practice that provides an economic benefit to the company or the owner of the trade secret. Google’s ranking algorithm is a good example.
Except for individual employees of this technology giant, no one knows precisely what the algorithm is, and Google itself patents only certain of its components, for example, Page Rank.
The trade secret has no expiration date. It doesn’t need to be published, so it can be stored indefinitely until another company discovers them. For example, a technology company has developed an optimal business architecture for its product and keeps it under wraps until another company finds it.
The weak link in the chain of secrecy is usually employees. Therefore, companies include non-disclosure agreements in the contracts of all employees who may deal with secret information.
Learn more about the difference between IT Security vs IT Compliance.
Intellectual Property Management Principles
Efficient and strategic management of intellectual property comprises three essential elements:
1. Protection
Methods of protection are becoming more complex, requiring a profound rethinking of the tools and processes they use. When choosing, it is crucial to consider which type of protection will be most appropriate and in which regions the intellectual property should be protected. Exclusive rights should remain with you throughout the entire product lifecycle.
Defensive publishing can be part of a complete IP protection strategy. By providing an accessible description of an invention to the public, with a proven publication date and authenticity, you protect yourself from two serious threats: patent trolls or non-practicing organizations.
They apply for patents to collect licensing fees or recover damages; also there are “partial fencing” strategies, when competitors patent additional enhancements to your core patent to reduce its value and enable them to license your core technology on preferential terms.
2. Process optimization
A strategy must be flexible and visionary enough to guide your organization through every step of the innovation cycle. Use your intellectual property strategy to optimize your approach to intangible assets, from research and development to patent portfolio management. Investing in the correct tools allows you to maximize your business’ intellectual property budget and allocate resources with confidence.
3. Assets monetization
Ultimately, IP strategy is judged by the value it creates for your company. Monetization is about more than just speeding up time to market with exclusive rights. A thorough portfolio management strategy improves your ability to identify violators and potential licensing partners. Strategic IP portfolio management can help companies identify adjacent or new market opportunities for new products or cross-licensing transactions.
Intellectual Property Strategies: How To Choose the Right One?
Developing the correct intellectual property strategy relies greatly on the organization’s maturity, and it must be flexible. It should include both competitor analysis and risk analysis and consider the company’s long-term business objectives. In addition, the strategy should cover all intellectual property, including technology, original content, concepts, trade secrets, inventions, and domain names.
An IP protection strategy may include a plan that specifies how a company will protect its IP rights in the event of infringement, such as pirated copying of one of its products or illegal use of copyrighted material. Most times, a combination of tactics is used that includes not only patents or trade secrets but also:
- Controlled access to service information;
- Data and software encryption;
- Copyright agreements and inventions signed by all contractors and employees;
- Non-disclosure agreements with external parties;
- Internal separation of Building Block technologies;
- Selective exchange of crucial information;
- Secure servers.
It is not unusual to use multiple forms of intellectual property protection to protect various aspects of the original creation, and this practice is called layering.
Special considerations
Most forms of intellectual property cannot be listed as assets on the balance sheet because there is no accounting for the measurement of intangible assets. However, the value of the property is reflected in the company’s price shares since market participants are aware of the existence of IP.
Some intangible assets, such as patents, are treated as property because they have a duration. These assets are recognized at a numerical cost through the amortization process. Depreciation is an accounting method that depreciates the value of an intangible asset over a specified period. This process helps the company write off a certain amount of tax annually as the life of the intangible asset decreases.
For example, a patent may only have 20 years before it is registered in the public domain, and the company will assign the total value to the patent. Each year for 20 years, the patent will be written off or amortized by the same amount – dividing the total value by 20 years. Thus, each year, the amount of depreciated assets will decrease the net profit or profit of the company for tax. However, perpetual IP, such as a trademark, is not amortized because it does not expire.
What Are The 3 Ways Of Protecting Intellectual Property?
In a 2019 survey by CNBC, one of five American companies admitted to having their intellectual property stolen. According to the Commission on Theft of Intellectual Property, the losses of American companies amount to $600 billion a year.
Therefore, protecting IP is so important. This is a complex task, which falls under the purview of legal, IT, HR, and other departments. We can give you some helpful tips on how we protect our intellectual property.
1. Determine what needs protection and why
Everything cannot be classified since not all information is valuable for firms to compete. So don’t waste your security resources or divert attention away from the proper security that is needed. Instead, identify the company’s IP assets and categorize them according to their vulnerability. Thus, only provide access to the vulnerable IP to key employees and restrict access or use to the core team. Sometimes, employees may only access a specific subset of protected ideas.
Asset management systems and internal security should be implemented so that managers can monitor who has access to secret information and maintain access logs. Also, system alerts that notify system administrators of suspicious or unauthorized activity should be implemented.
Securely encrypt and limit the number of copies of a confidential IP address, especially if it goes out to the outside world, such as on laptops. In addition, the IP address must be stored encrypted and backed up outside the building to avoid the risk of fire or another natural disaster.
Other significant steps include, for example, the use of non-disclosure agreements with employees with penalties in the event of loss of IP. Very often, intellectual property is leaked by mistake or because of incompetence. Make sure employees are aware of the potential for inadvertent IP disclosures. Constantly remind employees how, why, and why information needs to be protected, and alert them about the potential repercussions for the company if it escapes.
Nota bene
According to a study by Egress Software Technologies in 2019, most often confidential information leaves the company through the following channels:
- Corporate email (46%);
- Personal email, such as a Gmail or Yahoo account (51%);
- Collaboration tools like Slack or Dropbox (38%);
- FTP File Sharing (40%);
- SMS or other instant messengers such as Whatsapp (35%).
2. Develop effective measures to counter internal and external threats
Remember that there are two main types of cyber threats: outside and inside your IT networks. Therefore, your technology should intercept the actions of intruders at the earliest possible stage and warn them before the data is compromised.
The same goes for disgruntled employees or third parties who access your sensitive data and could harm your business. So the early detection of grievances and mitigation of their consequences is so crucial. Be loyal to all employees and contractors, especially those with confidential IP access, and don’t forget those who have been fired. Implement role-based access, review it regularly, and adjust access because of promotions, dismissals, reorganizations, or other changes in employment status.
Intellectual property can be attacked from outside sources. Cyberattacks and system hacks are the main reasons for losing confidential information from the outside.
As an IP owner, you ensure that strict security protocols are used for all systems, including the use of security monitors, firewalls, intrusion detection systems, and prevention devices.
Trade secrets stored in computer systems can be protected using encryption technologies or storage on servers without an external Internet connection. The servers on which the assets are stored should be something like the equivalent of a safe, and access to them should be as blocked as possible.
3. Be careful about the information you provide to your partners
Trade secrets and recent developments can be lost to business partners. To prevent this, disclosure of information should be limited as much as possible, even to partners such as contract manufacturers. In addition, the procurement of critical components must be diversified from different suppliers.
In some cases, the better way to protect your IP is not to patent it and treat your ideas as a trade secret. The patent discloses all the information needed to replicate your IP. And by law, it will only be protected by the countries in which your patent was issued, while everyone else will be able to use your IP freely.
In addition, your patent application can be granted to a pretty limited extent. In the meantime, your IP will be fully disclosed, and your competitors can use it or easily bypass it. Trade secrets have no time limits and are never publicly disclosed.
There is a risk that competitors will re-engineer your patented concept. Re-engineering is when competitors take apart or change an object or idea to reproduce it. Making certain changes to the original concept can lead to a “new” product or idea that competing firms can now patent as their own.
This way, they can avoid paying compensation for your patent idea and patent versions of your idea as their own. This often happens in the tech industry, for example, in the competition between Samsung and Apple.
How Copyrights Apply To Protect Source Code
Making source code is partly a creative process, so copyright law can protect the result of such work since the code can be considered as an original work of authorship. Keep in mind that code generation involves hundreds of smaller and more repetitive tasks that cannot be classified as unique and, therefore, are not subject to copyright protection.
This contradiction is often adjusted with the “Doctrines of Fusion.” Whenever the number of ways to complete the task is limited, developers’ or owners’ products are prohibited from using copyright to allow others to use the same techniques in your work. There are two critical aspects of source code protection:
- You must be sure that the source code is your intellectual property, not the developer’s.
- You should be advised that all technical details of your products are confidential.
How Can We Protect Your Intellectual Property?
Future clients of software development companies usually want to know how intellectual property is protected, and we will tell you how it is done in Jelvix.
The easiest way to protect procedures, ideas, methods, principles, systems, processes, concepts is to sign a non-disclosure agreement with your software development partner. A properly drafted NDA or confidentiality agreement implies that you can entrust information about your project to the development team and be confident in its security.
Usually, an NDA is signed at the very initial stage of cooperation. We can provide you with a custom NDA template or design an agreement that perfectly suits your business needs. You do not have to worry about disclosing any technical details or commercial information, as we legally guarantee the confidentiality of your data.
Jelvix follows best legal practices as defined by IP laws. A non-disclosure, which we usually sign at the client’s request, contains a clause stating that the disclosing party (the Client) owns the rights to all things that we receive as part of the cooperation (all code, ideas), including information they share with us.
Conclusion
Remember, intangibles are your long-term investments that will transform, promote, and support your business. And intellectual property rights allow you to lay claim to anything that is based on your original ideas. Since your ideas and creations have economic value, you must protect them and prevent any infringement of intellectual property rights violations.
If you need more information on how to protect intellectual property and how we at Jelvix protect developments for our clients, write to us today.
Need a qualified team?
Fill the expertise gap in your software development and get full control over the process.