Exploiting database protection is a classical way of making a data breach. With a single injection attack, a hacker can interfere with users’ personal information, block the site’s or app’s performance, and cause irreparable reputation damage. Methods for database security attacks are more intricate with every year, but the good news is, so are protection mechanisms.
We think that today setting up a secure database is actually easier than it has even been. There are so many great tools and metrics at our disposal that we can find a specific weapon against any kind of attack. In this article, we’ll share our take on database security standards, threats, measures, and best practices.
What is database security?
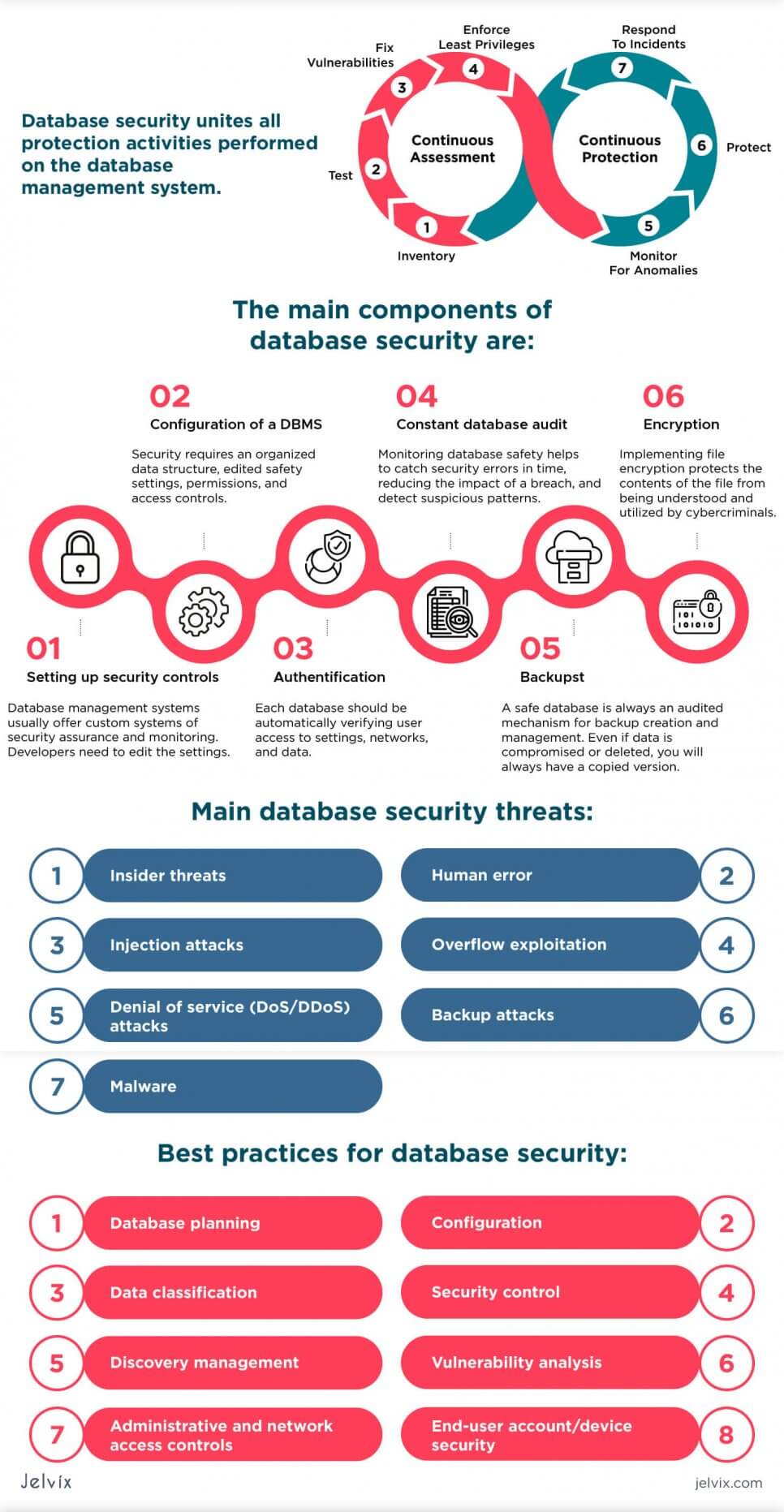
Database security unites all protection activities performed on the database management system. It’s responsible for the data layer of software architecture, its processing, transfer, and storage. The main components of database security are:
- Setting up security controls: database management systems usually offer custom systems of security assurance and monitoring. Developers need to edit the settings.
- Configuration of a DBMS: security requires an organized data structure, edited safety settings, permissions, and access controls.
- Authentification: each database should be automatically verifying user access to settings, networks, and data;
- Constant database audit: monitoring database safety helps to catch security errors in time, reducing the impact of a breach, and detect suspicious patterns.
- Backups: a safe database is always an audited mechanism for backup creation and management. Even if data is compromised or deleted, you will always have a copied version.
- Encryption: implementing file encryption protects the contents of the file from being understood and utilized by cybercriminals. Even if they get access to the database, the information itself won’t be displayed.
Database security is important for all databases, but even more so for large ones. Anderson rule states that a big database cannot be free from security issues; similarly, if data is easy and fast to access (the standard of many tech products), it won’t be truly safe.
Now users expect to get the app’s output after 1-2 actions, so databases hardly have ever been more accessible. With the increased adoption of personalization, even small businesses handle 10 times more data than 5-10 years ago. Usability improves, but the size and availability put security in jeopardy.
The importance of database security
Over the last few years, we’ve seen what happens when businesses fail to keep their sensitive information secure. Only in April of 2020 Godaddy, the Dutch Government, United Nations, and Defense Information Systems Energy had data leaks. With an increased percentage of remote work and data access, the chances of compromising corporate and organization security grows.
Big data breaches, like the ones in Uber or Equifax, make history and impact the company’s reputation long-term. Even an insignificant security crisis can have drastic consequences for the business.
- Compromising secret practices: if your company has unique technological inventions, creative work, strategic documentation, or trade secrets, the breach of this data will weaken your presence on the market and potentially strengthen competitors.
- Ruining reputation: today, many companies position safety as their main competitive advantage. Users become increasingly more aware of security risks and prefer cooperating with trusted businesses. Harris Poll survey showed that for 63% of people safety is a crucial factor in deciding on a purchase.
- Facing legal consequences: governments become aware of indecent data storage practices and push them on the legal level. HIPAA, Payment Card Security Standards, GDPR have million-worth fines for compromising user data.
- Bottlenecks: for data-based businesses, a breach means impossibility to continue their work and turn into downtime.
- Additional expenses: dealing with a safety crisis is a lot more expensive than preventing it. Additional spendings derive from increased costs of communication, security consulting, urgent development and testing, and crisis management.
Database security issues tend to accumulate. If you don’t tend to the safety of your data and DBMS, threats will pile up, compromising your team’s and client’s safety, operations, and resulting in a much bigger breach.
Main database security threats
The main task of database security is dealing with data layer threats. It’s important to understand the risks of storing, transferring, and processing data. Knowing which patterns might jeopardize your safety, you can remove vulnerabilities before they cause an actual accident.
We analyzed the most common database security threats and their specifics: if you are protected from those, you are safe from 99% of all attacks.
Insider threats
It’s the simplest type of a database threat but also the one which is the hardest to predict. Basically, a person who has assigned access to the database and its settings leaks, damages, or deletes information – and there’s a number of ways how it could be done.
- Malicious intention: someone hijacks the official access to the database – it’s either an employee of the company or an authorized partner;
- Negligence: a person can accidentally share access to the database via an email or flash drive or after catching a virus.
- Infiltration: someone enters the team with the purpose of hijacking the company’s data – less common for small and medium businesses, possible for corporations.
The surest way of minimizing the risks of insider attacks is to regularly revisit database security standards and access policies. The company should enable access to the database only for people who need it directly for their work. Employees who no longer work in the company or vendors should not have full permission, if any.
Human error
Human error attacks are similar to insiders’ negligent threats. Usually, they happen when an employee’s social media account, email, device, or used software is compromised. The virus hijacks the system and receives access to the database as well.
This doesn’t happen all of the sudden – human error is common in companies that don’t inform employees (in 49% of all data breaches).
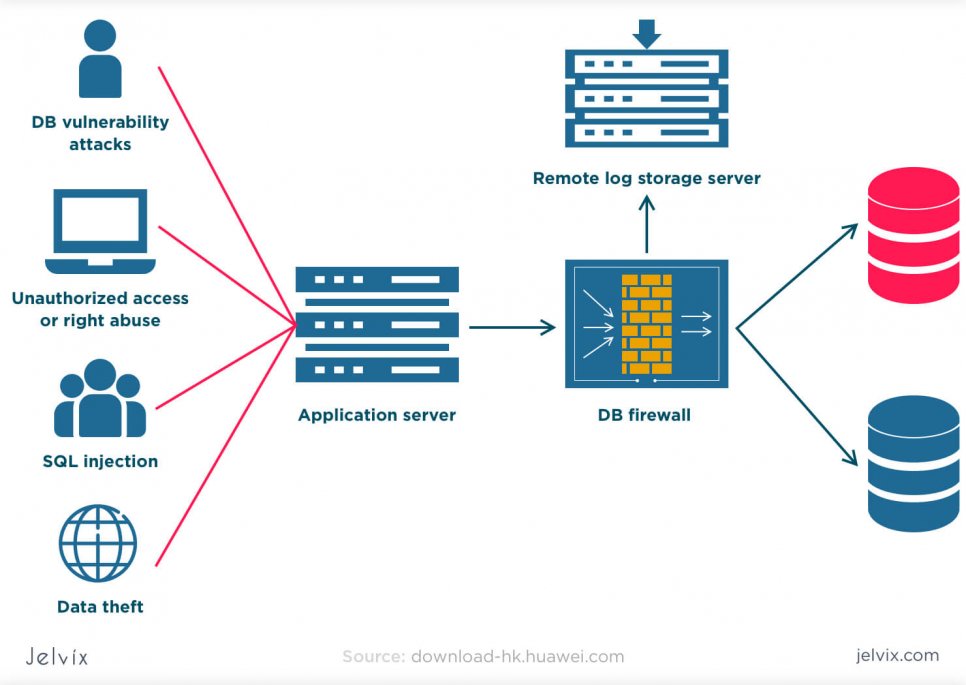
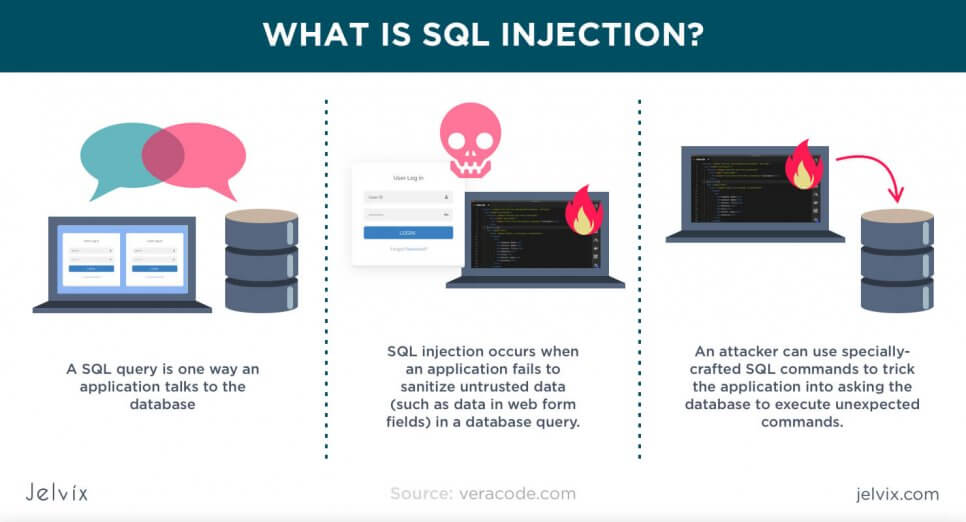
Injection attacks
If, in the previous two, any device, file, or software can be targeted, injection attacks are carried out specifically in a database or database management system. A cybercriminal inserts attack strings written in SQL or NoSQL into a database. The HTTP protocols and data layers of the application are compromised – since fake strings are seen by the system as the real ones.
To avoid this attack, companies need to monitor their data strings, regularly audit the database, and detect vulnerabilities. Simple security tests will quickly find such insertions and notify the team.
Overflow exploitation
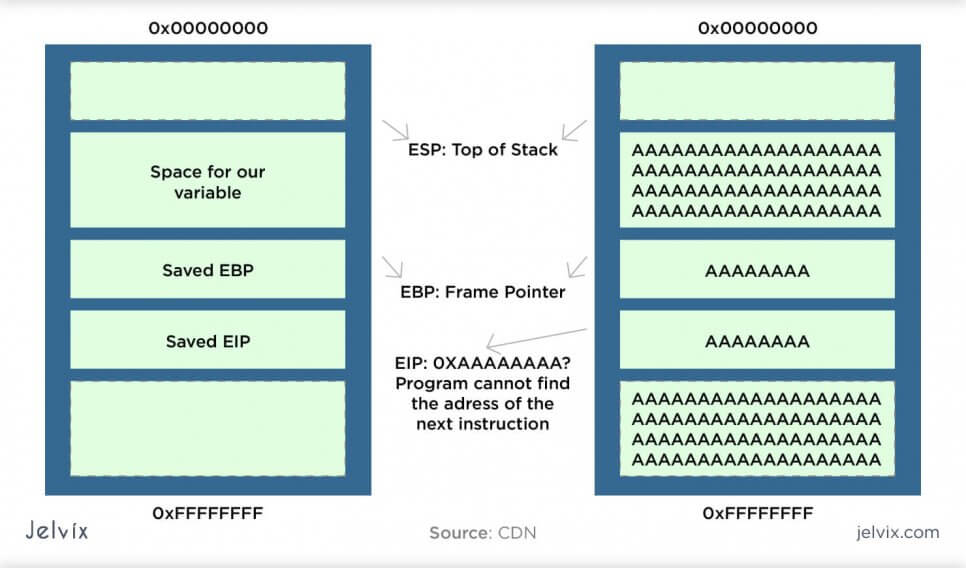
Sometimes the goal of security attack isn’t leaking the information but blocking the performance of the database – which will lead to compromised app performance. For instance, it can be performed on the e-commerce platform during a busy season in order to block check-ups, payment transfers, and registration.
Buffer overflow happens when a hacker runs processes overloaded with data. The block can’t hold the length of the request and stops responding. Several such attacks can be handled easily by the system, but thousands of faulty requests cause an overload.
The software, as a result, freezes. Just like injection attacks, this risk can be handled by visa constant vulnerability monitoring. A secure database should be
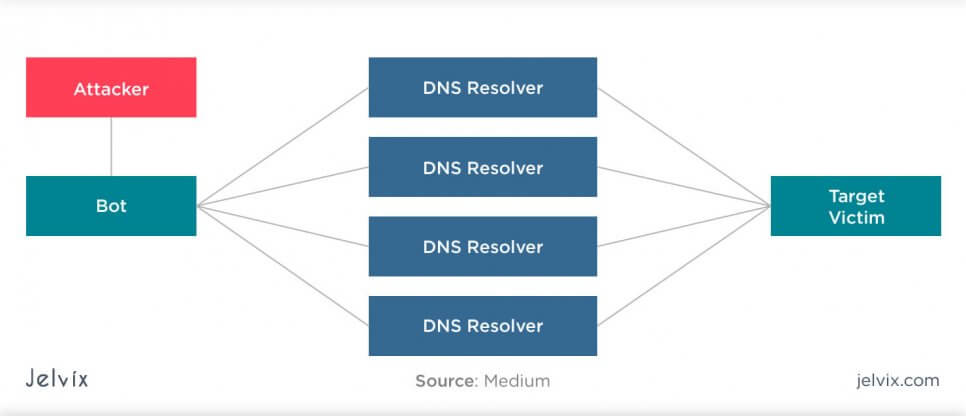
Denial of service (DoS/DDoS) attacks
If an attacker has a goal of blocking database performance, it can be done with many requests, not necessarily the long ones, like in buffer overload. At some point, the server can no longer handle that many data processing requests and shuts down. As a result of downtime, the company loses potential customers, revenue, and risks its reputation.
A distributed denial of service attack is even more dangerous. In this case, the increased number of requests comes from different devices and servers, typically located all over the world. It makes locating the source of threat a lot more difficult, and such attacks tend to last 3-4 times longer.
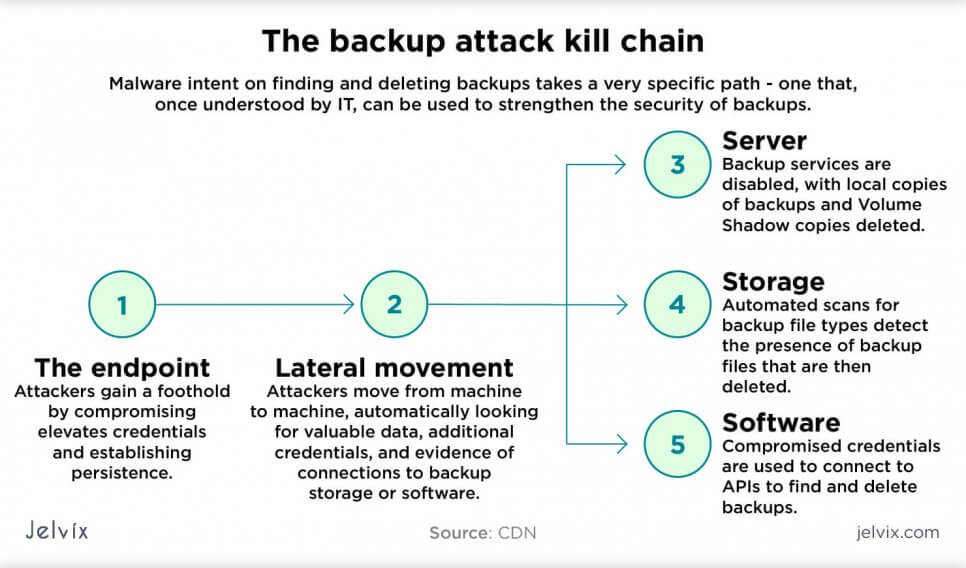
Backup attacks
Organizations usually aren’t too careful about securing their backup files. Often, they use the same methods and controls as the main database. If the main contents were compromised, an attacker wouldn’t take long to crack up the backup. Another common mistake is failing to protect the backup files altogether or not tracking their location properly.
Business is especially vulnerable to backup attacks if there are:
- Rapidly growing data massives: if the application scales quickly, the team likely doesn’t pay attention to the security of backup (they need to think about server load, performance, customer support).
- Branched infrastructures: when a system is large and distributed, teams don’t keep track of where backups of databases are stored or how they are protected.
- No cybersecurity experts: if the company doesn’t have a professional security consultant or in-house department, safety will eventually fall out of their priority list.
Malware
Organizations often face elaborate forms of database exploitation. Some attackers write malware for a particular database and send it to the endpoint devices connected to the network.
These most common types of database attacks can be stopped with simple security methods. Thorough inspection, control, and responsible approach to maintaining database safety are decisive factors in maintaining data security.
How are databases secure: best practices
Database security starts with planning and monitoring. If the company is aware of where and how the data is stored, they can monitor these sensitive areas more often, and detect dangerous threats in time. We are convinced that database security starts from having an established methodology – used technology is a secondary factor.
Database planning
The security of a database depends on many factors, but mainly on its type and size. Relational databases deal with structured tables of data, whereas non-relational ones are formed by descriptive documents. Ordering a relational database is easier because there’s no duplication. The data shares the same formats, and the relationships between information are clearly visualized.
- Take into account duplication: if you are using a Non-SQL database, it’s likely that pieces of sensitive data might repeat in various locations. Use duplication detection tools to spot and delete repetitive fragments.
- Remember that a bigger database size creates additional risks. The rule of thumb is, the bigger is the database, the more time and monetary expenses you need to estimate for securing it.
- Write a roadmap. Describe the steps of securing a database step-by-step. We’ll help you out with this one by listing all the essential activities in this checklist.
Database security planning entails recording the scope of the team’s activities, assigning responsible members, estimating risks and expenses, as well as analyzing the characteristics of a database itself.
Configuration
All settings and built-in controls of the database should be configured according to the best practices. For this, organizations typically hire a team of security experts that have experience working with particular databases and DBMS.
- Cleaning database configuration code: the teams need to review all the code that’s responsible for data layer settings;
- Editing user permission: checking the list of authorized people and updating it allows avoiding insider attacks and human errors;
- Checking network connections: if data migrates to and from Cloud or edge networks, the team needs to check the safety of connections, data transfers, and protocols.
Data classification
Not all data in a database is equally meaningful. Implementing expensive security measures on the entire database is an inefficient and overly ambitious task. Instead, the team should classify available information and create database security standards for it. It makes sense to first invest the resources and efforts in protecting the most classified data.
Security control
Safety control and monitoring are often enough to prevent the majority of database issues. Most security threats multiply and grow only because they were not tied and removed in time.
- Running safety tests: professional antivirus software and database security platforms will run check-ups to detect threats in the network;
- Developing a custom solution: corporations that handle large databases with classified data cannot rely on ready solutions – they often don’t fit the high specific needs of the company. In this case, it’s better to hire developers who can build a powerful personalized solution.
Discovery management
The core for database protection is usually laid on the discovery stage. Businesses should start cooperating with professional database security experts early on. At this stage, it’s worth bringing QA to the table – they will share efficient practice for product evaluation and testing.
- Writing security product requirements: a Software Specification Document should feature a section, dedicated to a database safety;
- Estimating the cost of a database breach risk: database security doesn’t only revolve around risk prevention, but also requires creating strategies for dealing with those problems.
- Analyzing security approaches chosen by competitors. Assessing good and bad strategies of handling databases during the discovery stage gives teams a practical idea of safe and potentially dangerous methods.
Vulnerability analysis
Detecting vulnerabilities is done via audits and monitoring. The team uses automated tools that detect suspicious patterns of behavior on all devices that are end-points for the database. It’s really important to not limit your security measures to a database in itself, but also secure all hardware that shares the access. All people who use a database should be aware of DOs and DONTs of maintaining database safety.
Administrative and network access controls
The fewer people have access to the database, the easier it is to ensure its safety. Similar logic applies to devices – the number of end-points should be cut to a minimum. Permissions should only grant rights for actions that are 100% necessary: no just-in-case scenarios.
End-user account/device security
Awareness is the key to maintaining a safe database. You should make a list of all employees and vendors who have direct or indirect access to the database. Also, run security audits on all devices that are connected to the database. Conduct security training with all employees who work with databases, especially regarding registration, authentification, and communication.
Controls and policies
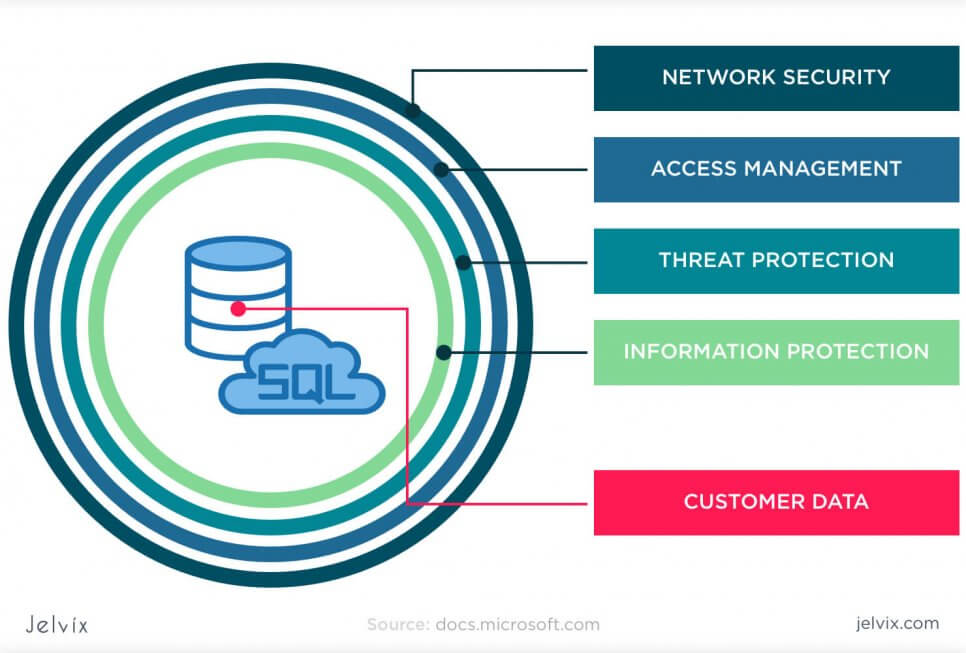
Database protection should be governed by organizations on the level of official documentation. We always define three key layers of controlling database security in our projects.
- Administration: documentation and guidelines that describe configuration management, database edits, and creation;
- Prevention: documentation about activities that revolve specifically around preventing security threats: access management, encryption, masking, etc.
- Detection: controls for monitoring database patterns and activities, identifying suspicious behavior, and data losses.
Designing database security standards that describe these three pillars of database securities allows companies to get a full view of their database security. You can refer to this documentation when you build new software, onboard team members, assign new access permissions, or choose vendors.
Let’s take a deeper look at the difference between relational vs. non-relational databases, their main principles and structure.
Examples of database security issues
Learning from big security breaches is a must for all companies who deal with databases. You can see the threats in action – as well as their long-lasting companies. There are hundreds of great cases to examine, but we stopped on four, which cover the most common threats.
NSA security breach: fabrication of protocols
The National Security Agency was breached by a system administrator, Snowden, by attacking trust certificates and the keys. Interestingly, NSA themselves used this strategy in Iran but failed to protect their own certificates. Snowden had admin permission, which allowed generating certificates and keys that were 100% native.
With SSH keys, the cybercriminal located needed files, gained access to classified servers, and collected the information. Because all these processes were executed with native keys and protocols, all transmissions passed off as authorized.
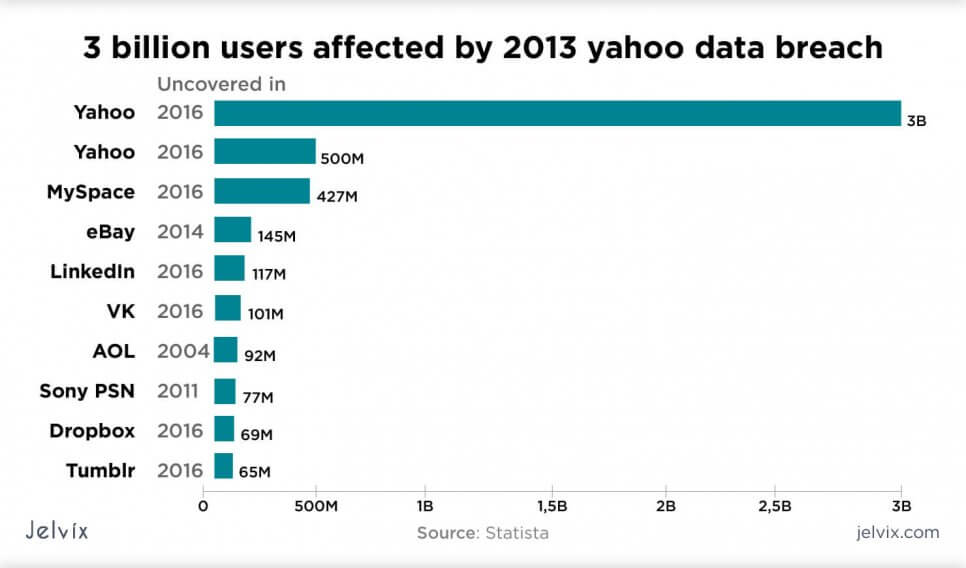
Yahoo (Social Engineering)
The network was hacked by Russian spies, who targeted a user database and an account management tool. Their breach compromised all 3 billion Yahoo accounts, becoming one of the biggest security crises in history.
Once hackers obtained access to the database, they found the entrance to the backup server and stole the backup files. It’s a classic example of an attack on copied files – because, as we discussed, their security is often overlooked.
The backup database had personal information and even cryptographic values. With these IDs, spies were able to locate particular accounts and access their full information.
Equifax
A data breach of Equifax happened in 2017 and affected 145,5 million users. The company literally pays the consequences even now – all people affected by the breach can file a claim up to 2024. At least 7 years of consequences and irreparable reputational damages – these were the consequences of one of the biggest breaches in history.
Equifax was showing signs of bad security as early as in 2016. Researchers were able to access a portal, reserved to employees, openly. Back then, they were able to download data from 10 million accounts in 10 minutes.
The problem wasn’t fixed properly, and in 2017, Equifax faced a number of breaches that exposed their customer database. The cause of the crisis was a failure to protect internal services and control database access permissions.
Uber
In Uber’s case, the thing that stands out to us the most is not even the breach itself – but the company’s strategy of handling it. Security matters are particularly handled by tech specialists (developers, testers, security experts), partially by managers, and also by the communication department. When all three don’t wok in sync, companies risk facing an Uber’s case.
The company was obliged to pay 148 million for their year-long miscommunication about a data breach. The fact of a data breach needs to be reported immediately – for Uber, it took a year. Such an approach is a clear consequence of the lack of thought-out documentation and protocols on data breach handling as well as a poor communication strategy.
This is why our tech experts always cooperate with management and communications specialists if there’s a crisis. All team members need to be on the same page and act according to regulations when it comes to security.
Conclusions
Database security is one of the main trends of 2023. Users and businesses are finally getting aware of the importance of having strong protective algorithms, and a professional safety team.
As a team that works with enterprises a lot, we have experience of implementing different types of database security on the large-scale level – and it has been a revelation to see that even large companies don’t take their safety seriously enough. For small and medium businesses, the issue has grown even deeper.
If you are planning on building software or already have a site or app, make sure your database is safe and revisit your information-handling practices. We are always happy to get on board – you can get in touch with our team and receive an expert consult.
Need help?
Scale your development capacity with top-level expertise and resources.