Data is an important topic these days for B2B companies. Running the business, you need to gather and analyze the information to achieve your goals. But there is the second side of this coin: being digital often means being vulnerable. Data is often called the new gold. Therefore it is not surprising that some people find databases of new goldmines.
With the growing popularity of smartphones, laptops, and other devices embedded with network connectivity, your data security is always under threat. With growing IoT opportunities, hackers receive the larger canvas on which to prey on. Global cybercrime losses and spending on cybercrime protection increased by more than 50% in two years to $ 1.1 trillion in 2020. or more than 1% of world GDP.
They become smarter and more creative. You don’t need to run a company like Google and Apple to understand the importance of data security. Even small B2B businesses can face security challenges, and we are ready to share the most useful tips you can follow to protect yourself.
Types of Cybersecurity Threats for B2B
As we are going to tell you about B2B security, you may wonder: what is the difference between it and B2C? The answer is simple: when it comes to a typical B2C business, scammers don’t care who their target is. They are just trying to reach as many companies as possible and earn money. And when it comes to B2B, there are 3 types of threats you can face:
- Random (about 90% of threats) — they roam freely and attack the organization by accident.
- Targeted (about 10% of threats) — their authors know whom they want to attack, what kind of protection does a particular organization use. So, they try to bypass it, penetrate the company, and act according to the circumstances. These attacks are often carried out through suppliers, and they are called supply chain attacks. It is when hackers infiltrate the vendor’s software first and then infect the company’s systems. Such attacks are pretty relevant these days since it is difficult to check all downloaded software. And this is another key feature of cyber defense in B2B: you need to protect not only your perimeter but everything that comes from outside.
Example: Hackers gained access to 15 thousand surveillance cameras in Moscow in 2020. Attackers plan to use access to 15 thousand cameras to create an alternative face recognition system, said a source from hacker circles. Vulnerable private cameras can be found by the search engine Shodan. A hacker using a search engine tip can gain access to cameras. - Cyberweapons (0.1% threats, or even less). These are attacks that are organized by such qualified groups that some people even have a suspicion that the attacks are sponsored by the state. These attacks are not meant to be profitable, and their main goal is to receive some information or ruin a particular business.
Why is it Better to Avoid Hackers’ Attacks?
Each business implements various IT solutions, and the more tools you use, the more likely you are to face cyberattacks and their destructive power. If hacking is turning out successful, scammers can reach all confidential information of the company and your clients and disable the company’s systems, thereby stopping your work.
You shouldn’t underestimate the risk of cyber attacks and the magnitude of the damage. It means denying the facts and putting the business at risk. The damage from cyber attacks can be economical, reputational, and legal.
The business’s financial losses are due to corporate financial information theft, such as bank details or payment card details. Black-hat hackers can steal both company funds and money from customers’ bank cards. Reputational damage is when you lose the customers’ trust.
In terms of legal liability, data protection laws require businesses to safeguard both customer and employee data. If the necessary measures have not been taken and the information is compromised, the business is threatened with fines and sanctions.
For companies operating in Europe, the consequences are especially unpleasant: according to the GDPR (General Data Protection Regulation), fines can reach 20 million euros or 4% of the annual business turnover.
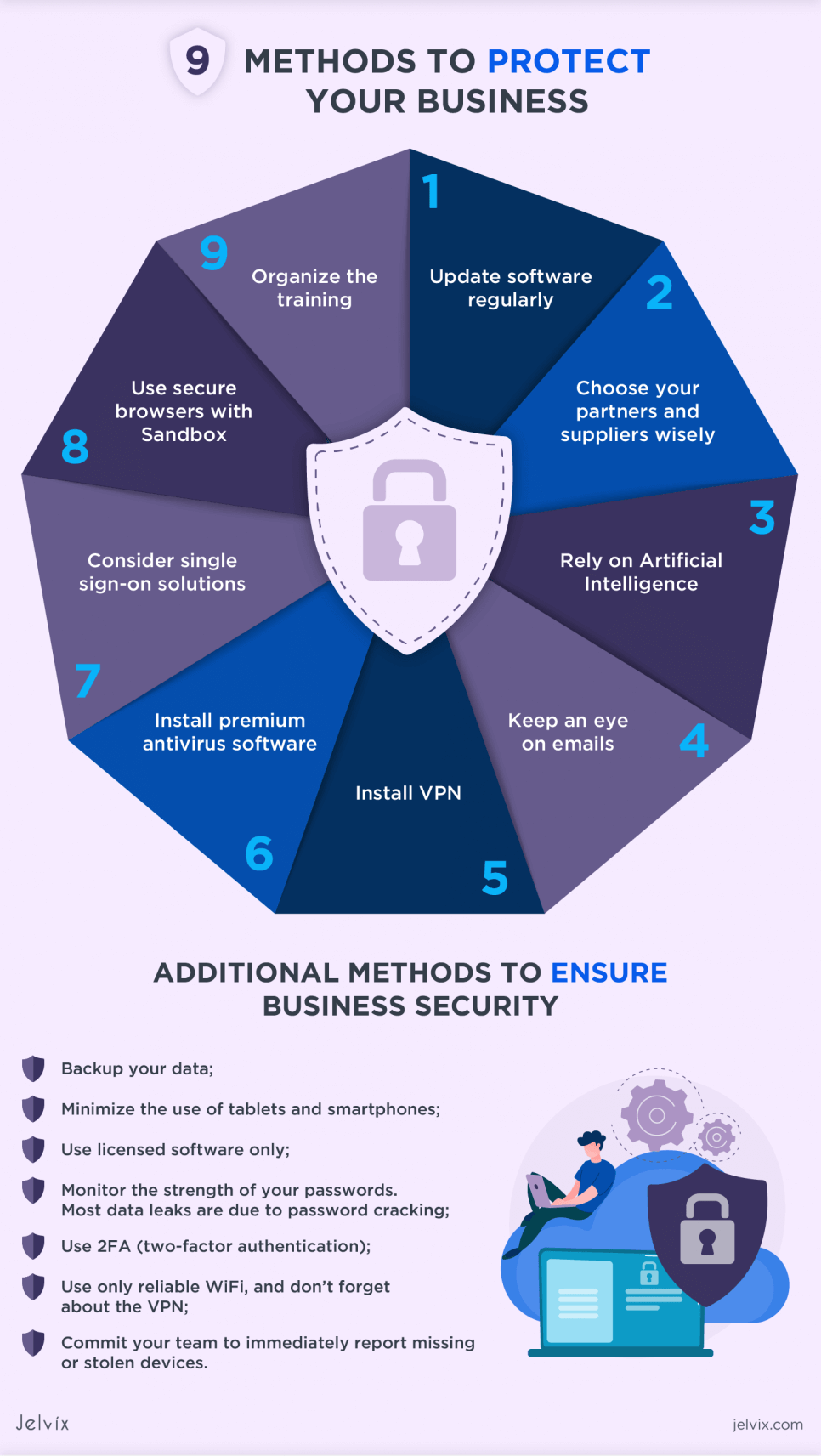
9 Methods to Protect your Business
As you may understand from the previous sections, the chances are that you will face the first type of hacking attack: the random one.
It means that even if you don’t have competitors who hate you or the company that wants to steal your data, you still need to find out as much information about cybersecurity as possible: what are the methods of social engineering, what is a double VPN, how to hide your IP from third parties, and what exactly can you do to ensure your company, your employees, and your customers are in safety?
1. Update Software Regularly
Let us guess, each time when you receive the pending update, you just hit the “remind me later” button, and this “later” never comes. It is definitely a wrong move if you want to build a really secure business.
Developers work on new versions of software, not just add some bells and whistles. They are continually trying to make applications more protected, including reliable security measures. And if you don’t update your operating system or some tools on time, you provide hackers with an opportunity to reach your device through infected software or compromised websites.
Twitter was concerned about updating its security system after a cyberattack in 2020. Twitter was hacked by hackers from the United States and Britain. According to the New York Times, the attack was hacked by a user nicknamed Kirk.
The leader of cybercriminals is a social media employee. It was Kirk who withdrew funds from the wallet where the scammers asked to transfer bitcoins.
The FBI is investigating a massive Twitter hack. The pages of Barack Obama, Kanye West and Apple were attacked.
In all profiles, hackers called for bitcoins to be transferred. Cybercriminals have promised double the return of the cryptocurrency.
If you see that websites and applications have various integrated components, you should know that they require additional debugging. By giving them regular updates, you avoid security issues.
2. Install VPN
A professional VPN service can mask your IP address so you stay out of sight of any intruder. However, it can also offer a wide range of services for individual and business security.
The company has dozens of servers worldwide, which means you can virtually change your location to overcome bans, get free access to regional content, and even provide direct protection for your device and your connections when working online through unreliable public WiFi.
Therefore, hackers don’t see you, and they can’t attack your constantly changing IP.
It can help to protect your devices, as well as your android phone. Users of millions of Android devices could face a cyberattack due to the vulnerability discovered.
Cybersecurity experts have assigned the issue a high severity rating. The vulnerability is noted to be in the Qualcomm Adreno GPU driver. It occurs when a user device structure is associated with kernel graphics support level (KGSL) file descriptors.
However, as experts explained, it is quite difficult to attack a device through this “gap” in practice.
Ask your employees to download the VPN so that the whole team is reliably protected from the attacks.
One more opportunity you can try is the double VPN when your online activities are hidden behind two servers, not one.
3. Rely on Artificial Intelligence
AI is the future of the Internet of Things, and it affects cybersecurity. Forbes’s study shows that 61% of companies use AI technology to identify and eliminate breach attempts. The 3-tip apps of AI these days are in:
- cyber defense;
- malware prevention;
- advanced threat detection and prevention.
If you work with the AI-powered security system, you receive an opportunity to mention suspicious threats in advance. So, think about increasing your budget, and look for a list of necessary tools.
4. Keep an Eye on Emails
It is perfect if you have a VPN or any other software to protect your computers from the intervention. However, it doesn’t mean that you should relax without considering the most likely sources of threats. Such as email. It is related to you personally and all your employees as well.
Anyone who has an email account receives spam messages from time to time. Some of them are easy to recognize, but we have already mentioned that scammers become smarter. Phishing emails are often difficult to detect.
They trick readers into entering their login data and providing hackers with access to the system. One of your employees may think that it is a letter from a famous company (Arnazon instead of Amazon) or even from you.
For this purpose, it is important that all your departments receive training to help them understand a double VPN, detect phishing emails, and what they should do when they receive a malicious message. This issue is especially relevant during the pandemic, when people work from home, using their personal computers that are not protected enough.
As an example, the World Health Organization (WHO) has been hit by a series of cyberattacks since early April. Employees of the organization received phishing emails, Bloomberg reported on Thursday, May 7.
The attacks began on April 3, the letters contained links. When navigating through them, malicious software could be installed on users’ work computers. Some of the emails were in the form of interview requests or newsletters about the coronavirus.
5. Choose Your Partners and Suppliers Wisely
B2B companies rarely work alone. To provide your customers with decent products or services, you need to collaborate with other companies, e.g., with cloud storage services, credit card processors, etc. And it is important to understand that these third parties may be dangerous for your business, even if they don’t know about it.
For example, if the unreliable cloud storage service doesn’t take care of its security features, what does it mean for you? It means that one day you may find out your files and data open to everyone. Credit card processing systems can be even more dangerous since it affects your customers if they are poorly-secured.
So, you should understand that it is not enough to have a double VPN and other useful software tools when you partner with companies you don’t really trust.
6. Install Premium Antivirus Software
We all know that antivirus is the first program you should install on your computer or smartphone. However, it doesn’t mean that you can just download the first app from the App Store or Play Market, and that’s it.
It would be a better idea to conduct some research and understand which antivirus software provides the necessary features. Most likely, it will be a paid plan but think about it as an investment. If this tool protects you from scammers and malware, it saves you a lot of money.
There are many factors that can affect your final decision, so ensure that you’ve considered all of them. You should also understand that the flu vaccine does not protect against other viruses. The same is with antivirus software: it does not always save you from worms, Trojans, ransomware viruses, keyloggers, spyware, rootkits, and other malware. Therefore, you can’t just choose one method from this list.
The Canadian company Bombardier has undergone a cyberattack. Attackers gained access to data about employees and customers. Information on 130 workers in Costa Rica became available to hackers. Production was not interrupted during the attack, the company said.
You need to install a set of B2B software tools to protect your company.
Learn more about database security standards, threats, measures, and best practices here.
7. Consider Single Sign-on Solutions
Running a business, most likely you’re constantly busy handling various tasks to create better products, earn more money, manage the team, etc. That’s why it is not surprising when businesses forget to update passwords across the company. And it may be a huge opportunity for hackers who are looking for a way to attack your business.
So, to escape this issue, you can rely on single sign-on solutions that are able to provide you with a guarantee that all passwords are updated on time, that they are strong and complex enough. You shouldn’t leave the space for human error since smart attackers will mention this vulnerability at once. And of course, they won’t miss the moment.
8. Use Secure Browsers with Sandbox and Other Secure Technologies: Chrome, Edge, Chromium-Based Browsers
In modern browsers, processes that need to directly “communicate” with the OS (computer file system, registry, utilities) are separated from those processes that don’t need such interaction. This technology is called Sandbox because the most confusing and often leaky code runs in a limited environment – like a Sandbox.
Even if the code reading the web page contains errors, the process cannot access OS functions such as saving the executable file or running it. To get out of the Sandbox, hackers need not one but several vulnerabilities. All of this increases the cost of a browser attack.
9. Organize the Training
The argument for cybersecurity training for employees is simple: if your team doesn’t know how to recognize a security threat, how can they be expected to avoid, report, or eliminate it? They cannot.
To make employees want to go through both testing and training, use references to real life and “horror stories” not related to work processes. Everyone is afraid that their Instagram profile will be taken away, copies of their passports will be downloaded from their email, or their bank account will be reset.
To prevent this, at a basic level, it is enough to understand what a strong password should be, and enable two-factor authentication everywhere, so that you could get into your account only after receiving an SMS confirmation.
Suppose an employee gets used to keeping an eye on their cybersecurity and realizes the importance of the simplest rules. In that case, they will no longer obstruct their implementation at the corporate level.
The new CEO of Uber, Dara Khosrowshahi, did not disclose information about a powerful cyber attack, as a result of which the data of 57 million customers and taxi drivers, were stolen for about two months.
As The Wall Street Journal reported, hackers attacked Uber’s database in 2016. The new director learned of the attack two weeks after taking office. Khosrowshahi ordered an investigation before making the incident public.
The companies disclosed information about the cyberattack to the Japanese conglomerate SoftBank, which planned to invest about $ 10 billion in Uber. The personal data breach was publicly reported only after two weeks of the accident.
Additional Methods to Ensure Business Security
There are a number of measures that can help a company secure its data. Here is a brief checklist with the most popular recommendations:
- Backup your data. Fortunately, these days you can store a backup copy of data outside the workplace and gadgets. Cloud services provide you with the opportunity to access it whenever you need it, even if the data on the work device is lost.
- Minimize the use of tablets and smartphones. Mobile devices are just as vulnerable to attacks as computers and laptops. It is a reason to develop security rules for all your employees that prohibit working with strategically important information from a smartphone.
Google security experts said that hackers attacked iPhone users for more than two years. According to The Guardian on August 30, the hacks continued until January 2019, when Google experts stopped them.
Attackers infected smartphones with viruses through several negative sites. To pick up the program, the user only had to go to one of these web pages.
After that, cybercriminals have full access to the personal data of the iPhone owner – passwords from various services, data from the address book, message history in instant messengers and in Gmail email.
- Use licensed software only. And install updates regularly. Any software has vulnerabilities; developers regularly test it for errors and release the necessary patches. But pirated versions are deprived of this advantage. Not to mention, the pirated version may initially contain malicious code.
- Monitor the strength of your passwords. Most data leaks are due to password cracking. Therefore, the team must know what strong and weak passwords look like. It will not be superfluous to install password managers that will automatically generate and save them.
- Use 2FA (two-factor authentication). Two-factor authentication is double protection, and therefore it is really reliable. First, the system asks the user to enter a password, and then it also sends a confirmation code to another device (for example, an SMS to your phone). Even if an attacker picks up the password, one will not be able to log in since one doesn’t have access to the second device.
It is necessary for your social media accounts. For example, specialists of the American company Facebook have updated a “security problem” in a social network that has overwhelmed a few tens of millions of acres.
On the second half of the day on Tuesday, 25 September 2018, the team of our engineers discovered a problem with safety, affecting almost 50 million records of the press service.
“Hackers have the ability to steal Facebook access tokens, which they could then use to get their hands on people’s accounts,” said Facebook engineers who were investigating the problem.
- Use only reliable WiFi, and don’t forget about the VPN no logs that don’t save your data. Connect only to secure networks that are password protected. If you have to use a public network, check with the owner to see if the network really belongs to him. Do not open confidential or sensitive information using public WiFi. Hackers give their networks names that look like real, trusted networks. Be careful and make sure you are connecting to the correct WiFi. Otherwise, a hacker could gain access and control over everything you do online.
- Commit your team to report missing or stolen devices immediately. Working remotely increases the risk of losing or stolen devices. If this happens, be sure to immediately report it to the company’s security department to minimize hacking risk.
Wrapping Up
Even if you use the most reliable software ever, and your team is well aware of possible threats, it doesn’t mean they will follow these rules. There is always a risk of human error. And It is a moment where the boss should become the bad cop, and you need to develop a set of obligatory rules in your company.
For example, you can forbid your team to:
- Work on a PC with administrator rights. If you work on a computer with normal user rights, hackers will have fewer opportunities to affect the operating system. They will lose the ability to steal passwords from other users, which will make it harder for malicious code to spread over the network.
- Download programs from unverified sources. A lot of Internet resources are geared towards infecting computers. It is extremely difficult for an ordinary user to determine whether any changes have been made to the software one has downloaded.
- Insert personal flashcards into work computers. There are many ways to inject malware into a computer. For example, its autorun may be enabled, and executable files may be infected. Sometimes cybercriminals use a flashcard that looks like a keyboard device and is able to type the malicious code. The user will not even notice it.
So, we hope you understand that cybersecurity is a pretty important thing to consider. Follow our recommendations, and you’ll make your business safer.
Rachel Burnham professional in the cybersecurity sphere. Rachel currently works at VeePN VPN company. She knows the best features of VPN for small and large businesses. In addition, Rachel consalt companies on cybersecurity issues.
Need a certain developer?
Fill the expertise gap in your software development and get full control over the process.