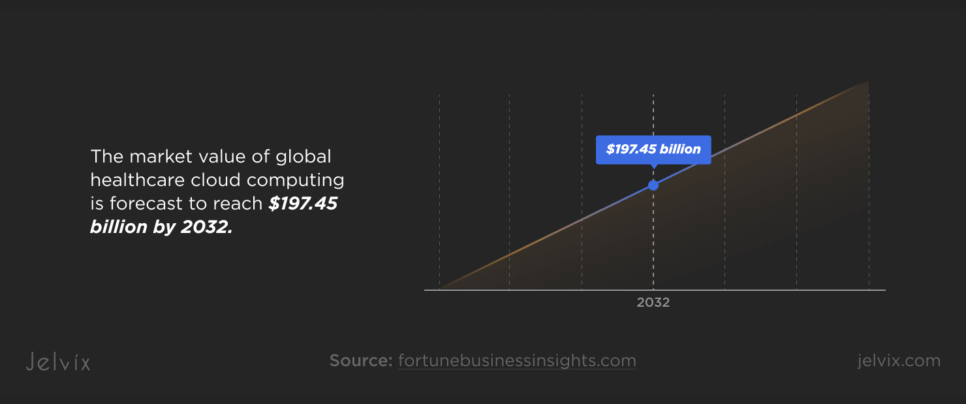
Due to the rapid adoption of cloud computing, the entire healthcare industry’s landscape is undergoing radical remodeling. With the market value of global healthcare cloud computing currently running at $46.55 billion and forecast to reach $197.45 billion by 2032, the shift in its nature is both inevitable and revolutionary. This exponential growth, at a compound annual rate of 17.5%, highlights the sector’s embrace of cloud solutions to enhance efficiency, scalability, and patient care.
However, the road to cloud integration is not without obstacles. Even though hybrid multi-cloud models aim to offer flexibility and resilience, 96% of organizations still face significant challenges in implementing cloud strategies. For healthcare service providers and IT decision-makers who wish to implement cost-efficient cloud solutions, three significant concerns are controlling costs, guaranteeing security, and bridging the skills gap in cloud computing.
Cloud security in healthcare, in particular, stands out as a critical pain point. The most recent surveys show that 85% of organizations say security-related issues are their first concern. Privacy and confidentiality of data head the issues list. For an industry that holds sensitive patient data, the stakes could hardly be greater. Missteps such as cloud misconfigurations—82% of which result from human error—can lead to devastating consequences, including data breaches, which average $4.35 million in costs.
Despite the urgency, only 20% of organizations assess their cloud security in real time. Most of the providers rely on human labor. The actions are manual and, therefore, prone to human error; 93% of companies are concerned that those using manual processes might inadvertently expose their data. With 29% of companies expected to increase cloud spending in the next 12 months, the pressure to cut costs without compromising security will only grow.
This article delves into the complex landscape of healthcare data security. We’ll explore the challenges, dissect the risks, and highlight actionable strategies to safeguard sensitive data while leveraging the full potential of cloud computing.
How Cloud Security Works in Healthcare
Imagine the cloud as a high-tech vault. It doesn’t just store your data; it protects it with multiple layers of defense. Those layers encompass encryption, identity authentication, real-time data flow monitoring throughout the network, and ensuring data consistency—a critical factor in the healthcare domain. Together, they form a robust security framework that keeps hackers away and sensitive data safe. But data cloud security isn’t just about fancy tools. It’s also about strategy tailored to the challenges healthcare organizations face.
When it comes to cloud data security in healthcare, there are five key components every organization needs to get right.
Compute Resources
- Virtual Machines (VMs): Allow the execution of applications and services just like real computers. Protection of VMs refers to their safeguard against threats and unauthorized access.
- Containers: Package the applications and their environment, providing consistent performance across varied computing environments. The isolation offered here adds one more layer of security.
- Serverless Functions: Are event-driven and ephemeral, reducing the attack surface. To protect them, security protocols need to be robust.
Storage Solutions
- Object Storage: Used for unstructured data. The security measures ensure that access is authorized and information breaches are prevented.
- Block Storage: Mainly used for databases and applications. Its encryption and access controls are locked down to ensure integrity and security.
- File Systems: Hierarchical structures demanding strict controls to prevent unauthorized alteration or deletion.
Networking
- Virtual Private Clouds (VPCs): Isolated environments that need proper configuration to avoid vulnerabilities.
- Content Delivery Networks (CDNs): Distribute content globally, demanding secure data transfer and protection against DDoS attacks.
- Load Balancers: Distribute network traffic and need protection against breaches or traffic diversions.
- Web Application Firewalls (WAFs): Enable the configuration of additional rules for greater protection of incoming and outgoing traffic.
Identity And Access Management (IAM)
- User Roles: Specify actions of users or the system to reduce the impact of a breach.
- Policies: A set of rules and permissions determining who can do what in the access control system.
- Permissions: Determine resource access, which requires regular audits.
- Authentication Mechanisms: Multi-factor authentication (MFA) along with strong passwords shall be used to access any resource.
Management and Monitoring Tools
- Cloud Management Consoles: Interfaces for overseeing resources; secure access is essential.
- Logging: Tracks activities to identify anomalies or threats.
- Alerting Systems: Notify stakeholders about security incidents for quick responses.
Detection and Response
Identifying potential security threats and responding effectively to mitigate risks.
Tools/Technologies:
- SIEM;
- Incident response platforms.
Here’s the tricky part: cloud security isn’t an across-the-board solution. Every healthcare organization has a unique mix of electronic health records (EHRs), telemedicine platforms, and other digital tools. The challenge is seamlessly integrating cloud security into these systems.
This is where shared responsibility plays a role. It could be called a partnership. The cloud provider secures the infrastructure, while the healthcare organization secures data and applications.
Cloud-native tools facilitate integration. For instance, automated compliance checks verify that your system meets regulatory criteria without you lifting a finger. AI-powered threat detection tools provide real-time insights and identify threats before they materialize. These developments are momentous for healthcare providers, who frequently manage limited resources and significant risks.
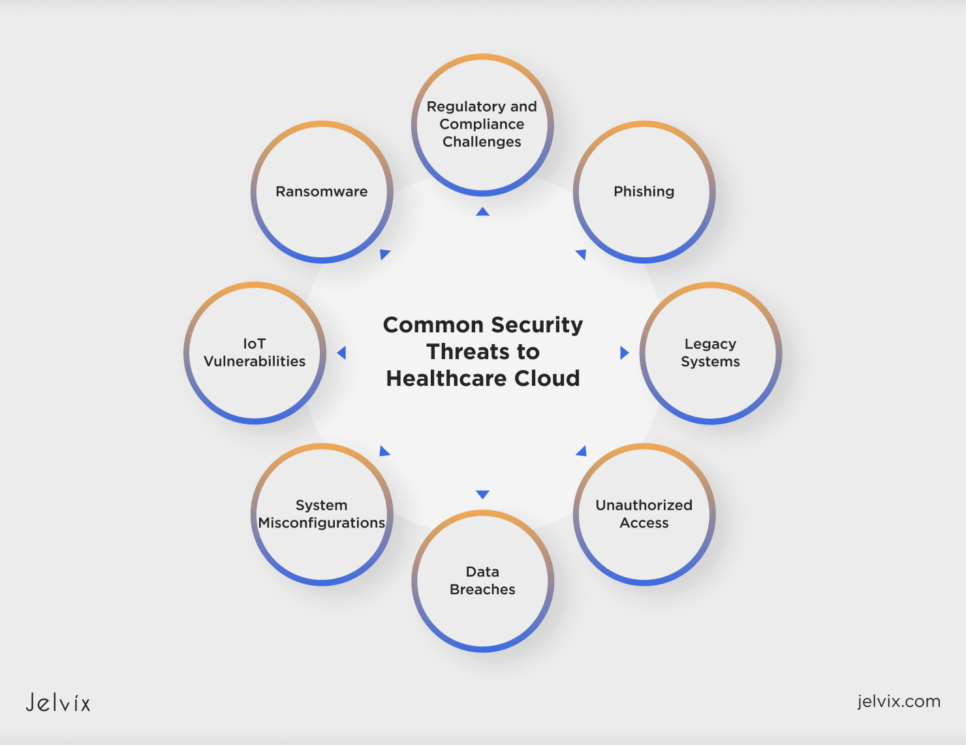
Common Security Threats to Healthcare Cloud
Healthcare companies are facing an increasing number of security risks as they continue to use cloud solutions. Knowing where the problem is—is the first step to finding a solution. The following are the most urgent dangers:
- Data Breaches. Due to its increasing volume, medical data is a hot target for cybercriminals. Currently, the world is facing horrendous consequences of phishing attacks and ransomware. In 2022, 61% of all medical care organizations reported at least one disruption related to cloud infrastructure. Scores of breaches are due to either weak security measures or insiders with unauthorized access.
- Unauthorized Access. Unauthorized access is a persistent issue. Cybercriminals exploit vulnerabilities in cloud resources, such as poor passwords, completely open APIs, and excessive permissions. More than half of healthcare institutions consider unauthorized access to be their biggest single source of security risk. Robust access controls and multi-factor authentication are essential to mitigate these risks.
- System Misconfigurations. System misconfiguration still sits on the throne as the top cause for all things wrong with security. Accidental slip-ups by employees can sometimes leave out sensitive or classified information. For instance, a senior administrator blamed a basic human error for a recent data breach in the health insurance exchange in Washington, D.C., which affected thousands of customers, including members of Congress. 56,415 current and past customers’ contact details, social security numbers, and dates of birth were among the sensitive data that were made public. Such mistakes highlight the importance of automated tools and regular audits to maintain secure configurations.
- Regulatory and Compliance Challenges. Navigating regulations is by no means simple. Healthcare providers must conform to frameworks like HIPAA and the GDPR while processing data across multiple jurisdictions simultaneously. The geographical spread of data centers in the cloud compounds difficulties; careful planning and ongoing surveillance are essential for maintaining compliance with regulations.
These are the most common healthcare data security challenges. However, with the rise of AI and IoT, the blow can come from rather unexpected sides:
- Ransomware: A relentless menace, ransomware attacks surged 81% in the past year. They target critical systems and electronic health records.
- IoT Vulnerabilities: Connected medical devices expand the attack surface. Poorly-secured IoT devices are set up as entry points for attackers.
- Phishing: The world has seen a 189% increase in phishing attacks, underlining the need for ongoing staff training to identify and counter email-based threats.
- Legacy Systems: Outdated IT infrastructure lacks the security to integrate with modern cloud solutions, exposing vulnerabilities.
If healthcare organizations take these challenges head-on, they can create a secure cloud environment. This will enhance the patients’ trust and be a possible point for innovation within an ecosystem of health care that benefits all parties involved.
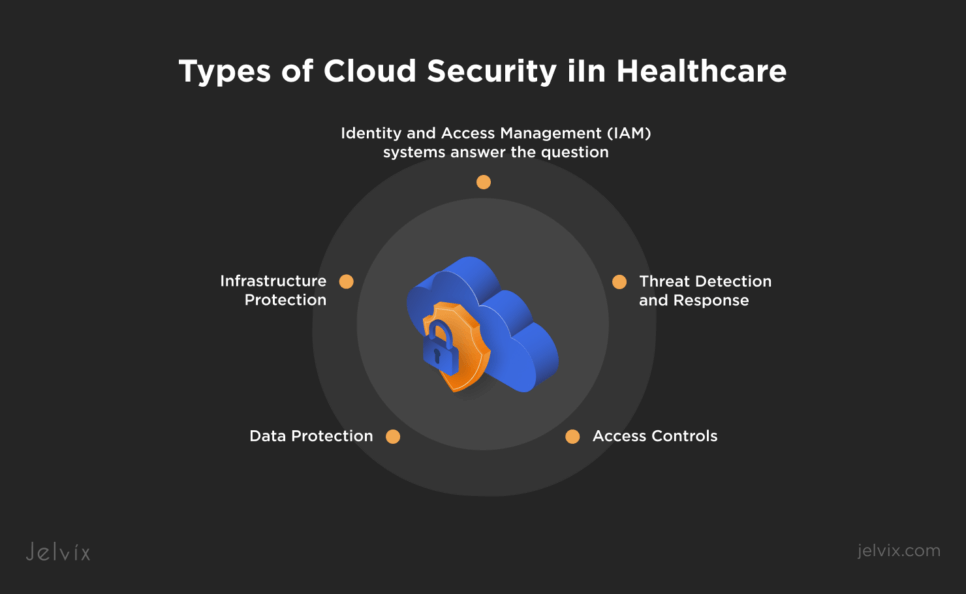
Types of Cloud Security in Healthcare
Several core pillars support cloud security in the healthcare industry, each intended to mitigate certain risks and safeguard private patient information. Together, these security measures provide a strong and durable structure.
- Data Protection: Healthcare runs on data, from patient records to lab results. Losing or compromising that data isn’t an option. This is where encryption takes the stage. It scrambles data, so even if someone gains access, they can’t understand it. You can think of it as turning sensitive information into a secret code. Healthcare organizations use encryption protocols such as AES-256 for data at rest and TLS/SSL for data in transit. Adding tools like data loss prevention (DLP) systems strengthens your defense against breaches. Moreover, to protect against SQL injections, which hack data in the database, protection is implemented through WAF (Web Application Firewalls), which is equally important. Resource policies are also employed for data storage, where critical healthcare data must remain consistent across systems to maintain its accuracy and trust.
- Access Controls. Access controls define who can access specific data and resources within the cloud environment. By building role-based access controls (RBAC), healthcare organizations can eliminate access for everyone but authorized users. This reduces the danger of insider attacks and unauthorized data leakage. For example, a nurse may be able to view a patient’s medical history, but only a doctor can change the prescribed medications. Only fine-grained access controls can adequately protect sensitive information from unauthorized disclosure.
- Infrastructure Protection. Every cloud system’s infrastructure is at the heart of servers, networks, and storage systems. This is something that cannot be compromised. In the meantime, intrusion detection systems and firewalls serve as sentinels, stopping unauthorized access before it happens. These tools also find holes in the system—fixing deficiencies early enough thinly avoids larger problems.
- Identity and Access Management (IAM) systems answer the question: Who gets access to what? Role and permission assignments ensure that only the right people can access confidential information. Multi-factor authentication, or MFA, adds another layer by requiring several identity validations for a user. This is similar to needing a keycard and a fingerprint scan to access a secured location.
- Threat Detection and Response. No system is invincible, so early discovery is essential. For example, Security Information and Event Management (SIEM) systems aggregate and correlate the information generated across the security events in the cloud. They collect and analyze logs from various sources, including firewalls, servers, and applications, to help detect potential threats. SIEM systems play an essential role in healthcare organizations by helping detect anomalies, kick off incident response, and drive regulatory compliance. Cyber threats can be centrally detected using SIEM tools, and mitigative actions can be taken faster.
When combined, these components help healthcare organizations create a multi-layered defense system. Data is encrypted, and users can interact with it only if IAM and access controls permit it. SIEM systems monitor activity and allow near-immediate insight into issues like hacks to prevent breaches. Collectively, these components create a holistic program to protect healthcare cloud environments and maintain patient trust.
Cloud Security Compliance for Healthcare
Regulatory compliance is not a box to be ticked. With healthcare cloud services now necessary for sensitive data management, compliance with different standards is key to preserving trust and protecting patient privacy.
- HIPAA (Health Insurance Portability and Accountability Act). HIPAA is the bedrock for healthcare data security in the United States, requiring strict practices to protect PHI (Protected Health Information). These include strong encryption, periodic audits, and access controls to limit unauthorized access. For example, PHI stored in the cloud must be encrypted with standards such as AES-256, and audit logs should register each access attempt made to sensitive data.
- GDPR (General Data Protection Regulation). For organizations operating within the EU or handling the data of EU citizens, GDPR emphasizes data privacy and security. For example, data should only be used with clients’ consent in decision-making involving their services. “Privacy by design” is mandatory to prevent potential leaks due to human error of unintentionally exposing sensitive information. If it is discovered that regulations have been violated at any stage in data processing, then this should also be made public immediately and clearly.
- ISO 27001. ISO 27001 provides a well-structured framework for establishing an Information Security Management System (ISMS). ISO 27001 ensures cloud-using healthcare providers have a methodical approach to safeguarding their sensitive information software, and it covers potential security risks using state-of-the-art controls such as data masking and key rotation.
- NIST Cybersecurity Framework. NIST offers a comprehensive framework for recognizing, safeguarding, detecting, reacting to, and recovering from cybersecurity threats. Cloud-based healthcare providers looking to integrate their operations with best practices in risk reduction and incident response would find it very helpful.
- HITRUST CSF. Some standards, such as HIPAA, ISO 27001, and NIST, are combined in the HITRUST Common Security Framework to create a thorough framework specifically designed for the healthcare industry. An organization’s dedication to putting sophisticated cybersecurity processes into place, from risk management to compliance monitoring, is demonstrated by its HITRUST accreditation.
Ensuring Compliance in Cloud Environments
Compliance in the cloud isn’t automatic. It starts with a partnership—healthcare organizations and cloud providers must work together under a shared responsibility model. The provider secures the infrastructure; the organization protects its data.
Audits and risk assessments are key. They’re the compass that guides organizations toward compliance. But they’re not enough alone. Automated tools offer real-time compliance monitoring, catching potential risks before they escalate.
Then there’s data residency. Patient data must stay within compliant regions. Providers offering region-specific data centers simplify this process, but organizations must ensure the rules are followed.
On the surface, compliance is about avoiding penalties. However, diving deeper, we see it’s about creating a system that patients and partners can trust. When healthcare providers embed these standards into every facet of their cloud security strategy, they’re building the foundation for a secure, innovative future in healthcare cloud computing.
Learn more about the types of data you need to protect and ways to prevent cyber threats at your clinics.
Best Practices of Cloud Security in Healthcare
Cloud computing in the healthcare industry has several advantages, such as flexibility, scalability, and cost-saving. But, as we’ve already covered, these are shadows cast by many security challenges. These challenges can be addressed with cloud security best practices that ensure sensitive data is secured. This will protect your organization from data breaches, enable compliance with regulations, and enhance trust from clients and partners with your business.
Implementing Strong Access Controls
Controlling who has access to private medical information is crucial. Employees can only access the required data thanks to role-based access controls, or RBAC. For instance, billing teams should only see financial data, while doctors may have access to patient records. Multi-factor authentication (MFA) adds a layer of protection, making it far more difficult for unauthorized individuals to gain access. Additionally, single sign-on (SSO) integration enhances both convenience and security, allowing users to access multiple systems with one set of credentials while maintaining robust access controls.
Regular Security Audits
Regular security audits identify vulnerabilities before they become threats. Assessment is directly related to the rules of compliance, and it ensures that as regulations and standards change, so do security policies. Tools like GCloud Healthcare API can also simplify the auditing process and yield actionable insights.
Employee Training and Awareness
Humans are often the weakest link in security. Well-trained employees recognize a phishing attack, know how to protect passwords, and handle sensitive information with caution. The educational program should also involve simulated scenarios right out of real life as preparation in addition to the training in the classroom.
Data Backup and Disaster Recovery Plans
For healthcare providers, data loss would be catastrophic. A robust backup plan ensures that critical data is never lost. Use off-site and on-site backups and test them frequently to ensure that data can be recovered without any problems.
Key Steps:
- Automate backups during low-traffic hours;
- Use geo-redundancy to protect against localized disasters;
- Regularly test backup integrity with dry-run restorations.
Engaging Data Security Experts
Healthcare organizations should collaborate with cybersecurity professionals to design, implement, and monitor cloud security strategies. External expertise ensures that emerging threats are addressed proactively.
Understanding the Regulatory Framework
Healthcare cloud providers must also enforce strict regulatory compliance such as HIPAA, HITRUST, or ISO 27001. Patient data is sensitive, and auditing and log collection must be sufficient enough from a secure patient data perspective.
Incident Response Plans
A well-defined incident response plan minimizes the impact of a security event. Measures include containment, eradication, and recovery steps.
Checklist:
- Assign clear roles and responsibilities;
- Conduct regular drills to test the plan;
- Update procedures based on lessons learned from past incidents.
Building a Security-First Culture
Security is not an IT issue; it is a culture. It requires leadership to dedicate and spend resources on cybersecurity, which ranges from hiring professionals to changing technologies and training programs.
Adopting these best practices will ensure that healthcare organizations remain proactive against emerging threats while fully harnessing the benefits of cloud services. It thus enhances not only the security aspect but also builds confidence and creativity in the pursuit of innovative approaches to patient care.
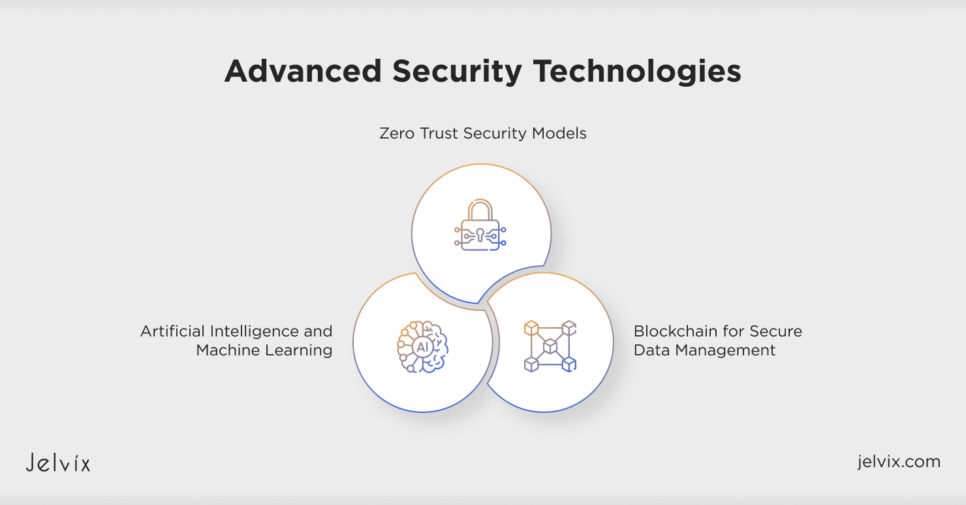
Advanced Security Technologies
Artificial Intelligence And Machine Learning
As cloud services for healthcare continue to develop, a higher standard of defense measures is required. AI and ML bring with them pre-active adaptive means of security. Employing neural networks, these technologies can examine terabytes of data to identify small anomalies that imply trouble ahead. Anomaly detection models, for example, spot odd patterns of access, such as one user downloading patient records in great bulk at odd times of the day and night. Organizations are then free to respond as they choose.
Predictive threat analytics, which identifies vulnerabilities in advance, is also based on machine learning models. A particular example involves clustering algorithms that examine EHR access logs to find internal threats, including employees accessing data unrelated to their duties. In addition, AI-powered natural language processing (NLP) tools can examine cloud configurations for misconfigurations, dramatically reducing human errors.
Blockchain for Secure Data Management
Blockchain technology has redefined how healthcare data is managed. It provides new forms of data storage–storage that is immutable and decentralized. Its cryptographic hashing guarantees that once data has been recorded, it cannot be changed. This makes it a formidable weapon against tampering and unauthorized alteration of information.
In healthcare, blockchain transparency allows for trustworthy, auditable transactions in medical data between institutions. Picture a patient’s entire course of treatment recorded on a blockchain ledger, accessible to any authorized provider across systems. This totally eliminates data silos, cuts duplication, and improves data integrity.
In addition, automated compliance audits have been made possible by smart contracts built on blockchains. An example is if there’s a HIPAA regulation and someone wants to view documents or logs (to verify their integrity), they must first request access rights from a service center. Only when these service centers verify the patient’s health data meets all requirements, can they gain entrance into terminals (like computers).
These automated checks reduce administrative overhead while ensuring adherence to regulatory standards. In addition, the interoperability problems that are so common in computer-supported or mobile healthcare operated across separate systems can be solved by blockchain. It provides a common ground for exchanging medical data between platforms and entities.
Zero Trust Security Models
Zero Trust architecture now challenges traditional network security paradigms, in which users and devices are trusted by default. In Zero Trust, every interaction is validated with a combination of identity-based authentication, continuous monitoring, and fine-grained access controls.
For healthcare cloud environments, Zero Trust insists on “least privilege” rules that ensure that users have only the resources they need. This method fits well with the IAM (identity and access management) system, and one of its other steps is multi-factor authentication (MFA). An advanced micro-segmentation scheme further protects cloud ecosystems by isolating workloads, helping to prevent a breach in one corner that can contaminate the whole.
Consider a scenario in which an IoT-enabled heart monitor pushes data from a patient to the cloud. With Zero Trust, the monitor is limited to a few endpoints, denying it access to other resources. Machine learning is a natural fit for this, overseeing access patterns and calibrating access in real time based on understanding risk.
Zero Trust also incorporates endpoint detection and response (EDR) systems to enable real-time threat containment. Thus, if an endpoint exhibits suspicious behavior, the system automatically quarantines it from the network to block any lateral movement, thus minimizing the potential impact of breaches.
By integrating AI, blockchain, and Zero Trust security models, healthcare organizations can construct a multi-layered defense strategy. These technologies enhance the protection of sensitive data and create an agile, adaptable security framework capable of evolving alongside emerging threats.
A Comprehensive Strategy for Healthcare Cloud Security
Analyzing the Current Security Landscape
Healthcare organizations must start by unpacking their current security architecture, taking stock of vulnerabilities introduced by cloud deployments, IoT devices, and expanded data storage. By utilizing such advanced threat intelligence platforms, they can analyze attack trend patterns and infer the strength of their existing defense mechanisms.
These testers and scans need to expand to cover cloud-native apps and APIs, and both threads need to be integrated without introducing new risks to operations. For example, less-monitored APIs may open doors for attackers to enter patient data housed in connected systems. Automated tools like cloud security posture management (CSPM) can highlight real-time misconfigurations and compliance risks.
Engaging Security Technology Experts
The intricacies of healthcare cloud environments necessitate collaboration with cybersecurity specialists. These experts deploy cutting-edge solutions like extended detection and response (XDR) platforms, which consolidate threat detection across endpoints, networks, and cloud workloads.
Additionally, technology consultants can design robust identity and access management (IAM) frameworks, incorporating biometrics and contextual authentication to enhance security. Their expertise extends to orchestrating incident response simulations preparing organizations to handle potential breaches with precision and efficiency.
Developing a Comprehensive Security Policy
A dynamic security policy forms the backbone of healthcare cloud security. More than mere regurgitation of access rules and encryption protocols, issues like data jurisdiction and third-party vendor liability need to be considered. For example, a policy should require selecting key management services (KMS) to handle cryptographic keys so that even cloud service providers cannot access such sensitive information.
From another perspective, policies should also integrate automated compliance tracking systems that implement machine learning to watch how exactly it all stacks up against frameworks such as HIPAA, PCI DSS (and now GDPR), or ISO 27001. By incorporating continuous learning mechanisms, companies can adjust policy to new regulatory settings and technological advances.
Continuous Monitoring and Incident Response
Real-time monitoring tools such as SIEM systems are crucial in identifying anomalies before they magnify. These systems aggregate logs related to cloud workloads, Internet of Things (IoT) devices, and endpoints, creating one view of the security environment.
Organizations must break out of mere containment; incident response plans must also make room for detailed recovery protocols. In ransomware attacks, for example, advanced forensics can determine the source of the breach, while secure backups allow operations to resume without interruption. These platforms automate the response workflow, assuring a decrease in downtime and lessening the monetary effects due to faster response actions.
This approach will enable healthcare providers to effectively counterbalance real-time monitoring with advanced incident response approaches, both critical components for medical data security and providing regulatory compliance and operational success.
Conclusion
Securing healthcare cloud environments is a multifaceted challenge that requires advanced technologies, strategic planning, and continuous vigilance. At Jelvix, we approach cloud computing for healthcare as a dynamic challenge, crafting solutions that don’t just meet today’s standards but anticipate tomorrow’s threats. Our healthcare software development strategies are engineered to adapt, evolve, and empower, addressing the most pressing security issues with precision and ingenuity.
What makes us different? It is our commitment to leveraging modern tools and best practices in building robust cloud infrastructures. We go beyond compliance to deliver transformative outcomes through advanced technologies. We advance Zero Trust architectures that limit access on a need-to-know basis, AI-driven systems that anticipate attacks before they happen, and blockchain frameworks that secure data fidelity in multi-cloud landscapes. These are not merely security measures; they are strategic advantages customized for your specific operational requirements.
Your cloud security deserves more than protection—it needs innovation. Contact Jelvix today to explore how we can redefine security for your organization and ensure safety, compliance, and trust in every patient interaction.
FAQ
Why is cloud security essential for healthcare organizations working with third-party vendors?
Cloud security safeguards sensitive patient information, even when sharing it with third-party vendors. An effective security framework reduces the risks of data breaches and regulatory compliance failures in these partnerships.
How can cloud security strategies improve operational efficiency for healthcare enterprises?
A strong cloud security plan lowers operational risks, guarantees data availability, and permits safer, quicker workflows, resulting in lower costs and more efficient operations.
What are the financial implications of a weak cloud security system for healthcare organizations?
An inadequate cloud security system may lead to regulatory fines, expenses for data breach recovery, harm to reputation, and missed business prospects.
How can healthcare companies ensure secure cross-border data exchange?
Organizations must adhere to international data protection regulations, utilize encryption protocols, and collaborate with cloud providers that offer data storage solutions tailored to specific geolocations to manage cross-border data exchange securely.
What are the trends shaping the future of cloud security in healthcare?
Innovations such as Zero Trust architecture, quantum-resistant encryption, and blockchain technology for secure data sharing are transforming healthcare cloud security. These developments aim to boost threat detection, strengthen compliance, and guarantee scalable, secure solutions that adapt to the changing needs of healthcare.
Need high-quality professionals?
Scale your development capacity with top-level expertise and resources.