Remote working is becoming more and more popular for a wide range of reasons. As a result, more businesses rely on cloud-based technology. Cloud computing has become widely used in project management, networking, and operations.
According to Cybersecurity Ventures, the total amount of data stored in the cloud, which includes public clouds operated by vendors and social media companies (think of Apple, Google, Microsoft, etc.), government-owned clouds accessible to citizens and businesses, private clouds owned by mid-to-large-sized corporations, and cloud storage providers, will reach 100 zettabytes by 2025. It means 50% of the world’s data at that time, up from approximately 50% today.
What are the advantages of cloud computing? And what are the risks that companies encounter when using cloud services? Let’s delve into the specifics and show you how to safeguard your company’s data from the most common cloud computing risks.
Cloud Computing Benefits and Risks for Your Business
Numerous organizations are undertaking technological advancement. It is one of the most powerful strategies to remain competitive in today’s crowded industry. Transferring your organization to the cloud will affect many aspects of your organization’s operations.
The cloud offers many advantages: from speed and accessibility to the absence of piles of paper. Moreover, there are different types of cloud service platforms, each having its own peculiarities. There is no doubt that this format of work has its risks. Let’s consider them and their solutions
The History of Cloud Storage
The concept of an “intergalactic PC network” can be linked to the beginning of cloud computing in the 1960s. Significant developments in the field of cloud computing occurred in the 1970s and 1990s.
As an illustration, IBM developed the VM (Virtual Machine) working framework in 1972. In the 1990s, a number of media companies provided their own variations of virtualized private systems. Cloud solutions are now divided into three groups based on their intended use: personal, public, and private.
What Separates Virtualization from Cloud Computing
Since about a decade ago, virtual machines have served as the primary computing unit in the cloud, enabling dozens of different apps and workloads to operate and develop successfully. Virtual machines depend on the hypervisor’s capacity to effectively distribute computing resources across hardware by decoupling them from it.
Virtualization is therefore the technology that makes it possible to build a number of dedicated resources or simulated environments from a single physical hardware system. Cloud computing is not a single technology, but rather a set of concepts and methods for providing consumers with on-demand access to platforms, services, and applications related to computing, network, and storage infrastructure across any network.
What Is Cloud Computing And What Are Its Advantages
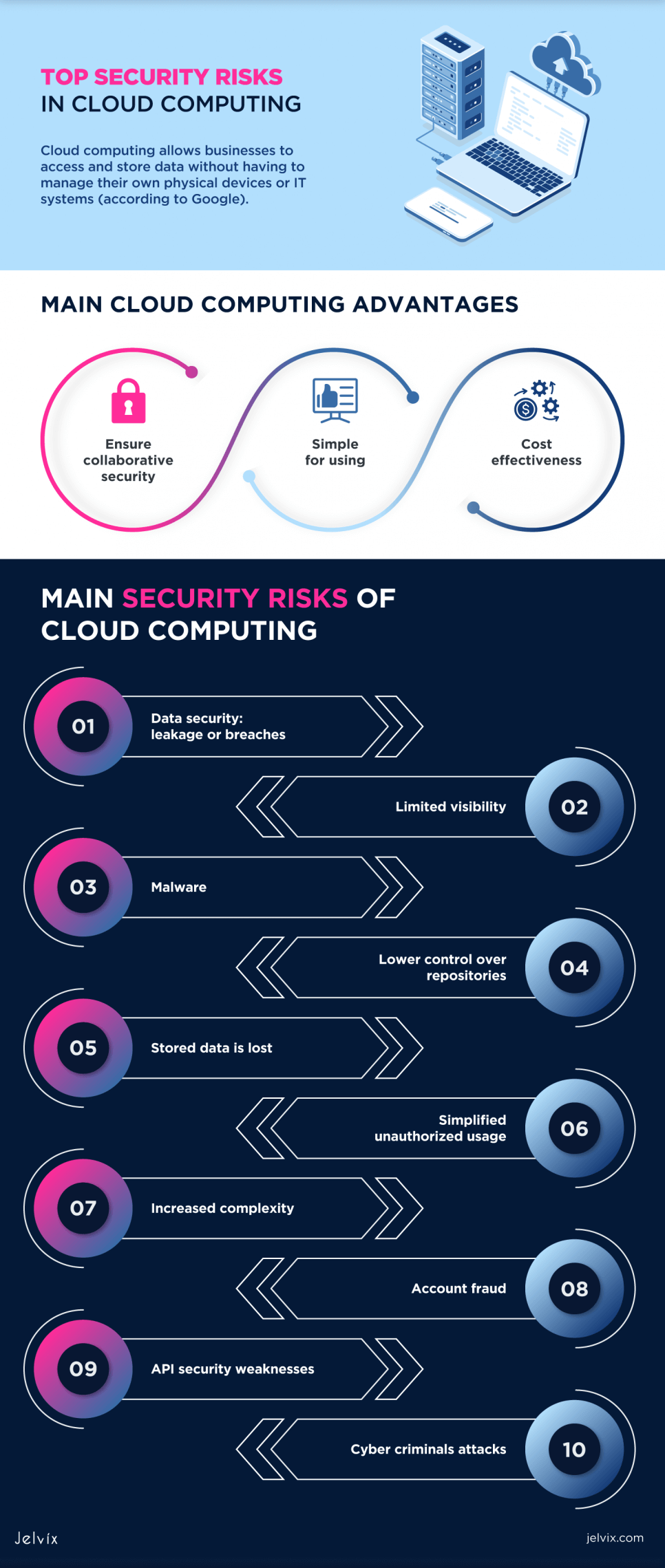
Cloud computing refers to the distribution of on-demand computer resources — hardware, storage, databases, networking, and software — via a network to organizations and people (usually the Internet). Cloud computing allows businesses to access and store data without having to manage their own physical devices or IT systems (according to Google).
Cloud computing services save time and assist with management. Users benefit from enhanced customer experiences and increased data accessibility. Investors can also get thorough updates on the company’s performance at any time.
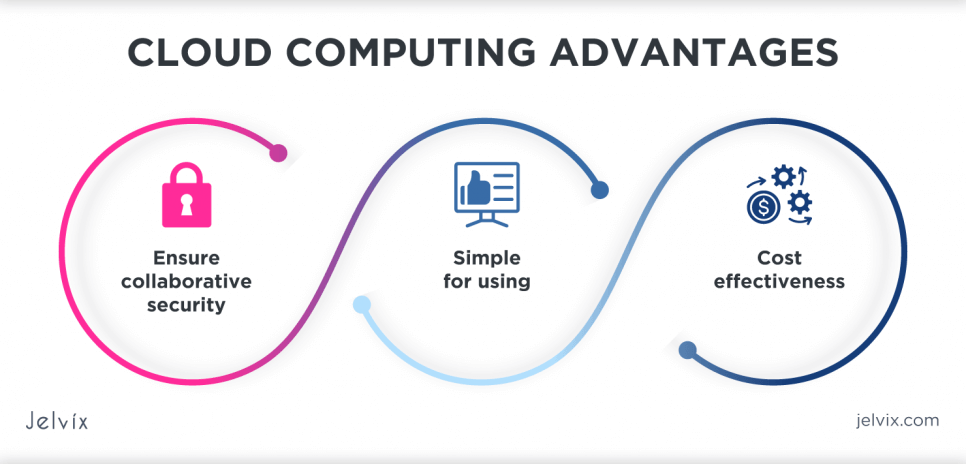
The main advantages of cloud services include:
- Ensure collaborative security. The cloud may be the greatest option for coordinating two or even more teams.
- Simple for using. Cloud computing enables instant data access, procedures, and important enterprise systems from any part of the worldwide with a stable Internet connection.
- Cost-effectiveness. Because cloud computing is a subscription model, there are no upfront costs for hardware, software, or maintenance.
- Shorter time to market. Developers can work more quickly with rapid deployments because new instances can be spun up or retired in a matter of seconds.
- Scalability and flexibility. Cloud computing gives your business more flexibility. Without spending money on physical infrastructure, you can easily scale resources and storage up to meet business demands.
The more data a firm has on the cloud, the more effectively it will recruit new clients, establish development strategies, and increase its market position.
For instance, cloud computing has become a development worth examining in the healthcare sector, where organizations display information on every patient, including symptoms, diagnosis, treatment, and a comprehensive medical history. Other industries are also adapting the cloud model to their needs and challenges.
Limitations of Cloud Computing
Traditional computing uses a hardwired connection to access data on servers or storage devices. Using cloud computing may result in inability to access the data or apps needed due to a bad connection. The use of the cloud has benefits and drawbacks, just like any other technology.
Other disadvantages of cloud computing include:
- vendor lock-in possibility;
- less control over the cloud’s underlying infrastructure;
- worries about security risks like data privacy and online threats;
- integration difficulty with legacy systems;
- unexpected expenses.
When moving to the cloud, there are many difficulties that arise because it is unclear what services the providers offer, how much they charge, and which security tasks still fall under the customer’s purview.
Let's find out how the Enterprise Data Warehouse can help solve big data challenges.
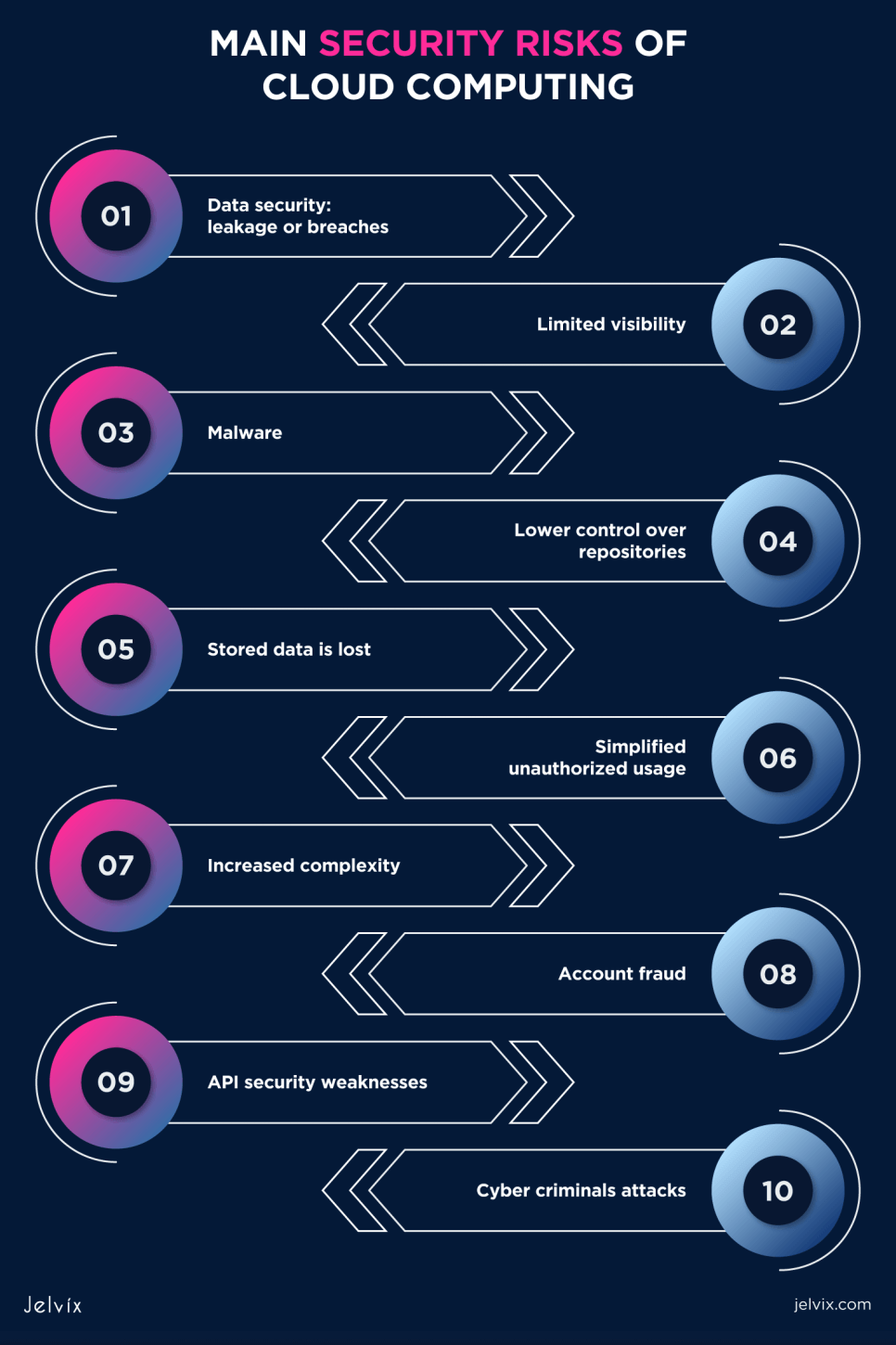
What are the Main Security Risks of Cloud Computing
Understandably, 75% of businesses rank cloud security as their top worry. 33% are extremely concerned, 42% are very concerned, and only 25% are indifferent to somewhat concerned. Let’s take a look at the most popular security risks you must be aware of before moving all your business data to cloud storage.
Data security: leakage or breaches
Over the same time period, over 53 million people in the US (2022) were affected by data compromises such as data breaches and leaks (according to Statista). It’s one of the most common risks of cloud computing. Not all providers of cloud services are capable of creating backups when required.
Limited visibility
Companies might lose visibility into system integration, resource, service consumption, and costs when they migrate their workflows and assets to the cloud. Organizations must use extra technologies to monitor their cloud services consumption, such as cloud security configuration monitoring, network-based monitoring, and additional logging.
Malware
As the prominence of cloud computing rises, so does cybercriminal activity. Malware (a portmanteau for malicious software) is any software that is intentionally designed to disrupt a PC, device, customer, or network node, leak personal data, obtain unauthorized access to systems or systems, deny access to that information, or interfere with the host PC’s privacy and security (according to Wikipedia).
Lower control over repositories
Different types of cloud service models offer varying degrees of resource control. You often have no influence over where your data is kept. When a breach happens, you may not even understand exactly whether it occurred or where it occurred.
Stored data is lost
This type of risk is possible in any system, not only CC. There are several ways to lose data in the cloud. When technology fails, systems halt and backup copies become lost. At times, servers fail and the data stored therein is lost. Although most cloud storage companies go to considerable measures to protect their networks and your data, not all assaults can be avoided.
Simplified unauthorized usage
Administrators, developers, and other trusted staff with access to sensitive data may unintentionally cause harm. Security risks aren’t just external threats. Cloud services frequently have publicly available URLs for uploading and downloading files, which can lead to data leakage if inadequate security protections are implemented.
Increased complexity
Cloud complexity is the outcome of the fast acceleration of data migration without regard for the difficulty it brings into processes. With public, private, and multi-cloud added to legacy systems, IT complexity grows.
The issue is that as workloads are moved to the cloud, IT does not remove endpoints (tech systems such as servers, databases, and so on). That is, when applications go to the cloud, the traditional platforms remain in some form. They are used less frequently, but they must still be regulated.
Account fraud
Thieves can get login credentials to access sensitive data stored in the cloud and are known to exploit holes in network architecture, thus using strong passwords that are updated on a regular basis is an excellent practice. The 3 major types of fraud:
- Misappropriation of property;
- Bribery and corruption;
- Deception in income accounts.
According to McKinsey & Company, synthetic ID fraud is the fastest-increasing financial crime in the United States.
API security weaknesses
When APIs fail to enforce correct access control, encrypt data, or sanitize its inputs, cross-system vulnerabilities can occur. Cloud services with unsafe APIs endanger information confidentiality and integrity, exposing your systems and data. Thieves often utilize three sorts of attacks to try to compromise APIs: brute force assaults, denial-of-service attacks, and man-in-the-middle attacks.
Cybercriminals attacks
Cybercriminals use a variety of strategies to launch a cyberattack, including phishing attacks and the use of stolen login information. In the remote work era, the endpoint is the primary target of cybercriminals and an organization’s primary defensive line.
Despite the ubiquity Management: security threats, statistics from Check Point reveal that 99 percent of businesses are not adequately safeguarded. A cyberattack, on the other hand, is avoidable.
How to Manage Cloud Computing Risks: Best Ideas
Now that we’ve discussed the main risks of moving data to the cloud, let’s take a look at the solutions that have been developed to overcome them.
Testing for cloud penetration
The goal of cloud penetration testing is to evaluate a cloud system’s strengths and weaknesses in order to strengthen its overall security posture. Cloud penetration testing aids in the identification of risks, weaknesses, and gaps. The consequences of vulnerable vulnerabilities. There are five types of penetration testing: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting.
Security training
To reduce the human risk aspect, you must provide cloud storage security training to your personnel. You can select an advanced course for those who will be in charge of the security and maintenance of files in the cloud, but for the most part, employees will need to understand the fundamentals of data protection in virtual systems.
Preparing for the unforeseen circumstances
It is a significant step to transfer all of the organization’s data to the cloud. With the help of your team and the cloud service provider, develop backup plans. The more possible difficulties you analyze, the more secure your personal information will be. If at all possible, you can also hire someone to manage and secure the cloud data for your business.
Data security audit
Cloud security is a shared obligation among cloud providers and clients. A cloud security audit is an examination of an organization’s security policies in place to secure its data and other resources in the cloud. An external auditor often conducts the audit, using various test scenarios and checklists to determine whether the target security posture is adequate.
The organization’s risk tolerance and the sensitivity of the data stored in the cloud determine how often security audits of cloud infrastructure are conducted. At least once per year, most businesses should conduct cloud security audits.
Designate a person to manage the cloud budget
Make sure your company has a budget for using cloud services to reduce worries about the higher costs associated with data migration to the cloud. Keep track of your spending and hunt for the finest chances, since the cloud industry is brimming with them.
Encrypt your data
Data encryption is a method of converting plaintext (unencrypted) data to ciphertext (encrypted). To store passwords and sensitive information, pick the encryption technique that works best for you. This will provide an additional layer of security.
Set User Permissions with Proper Passcodes
Different employees need access to different sections of the company’s files. It’s best to personalize access so that your staff members can access the files they require. For their accounts, it’s also crucial that they frequently come up with brand-new, challenging passwords. This will help protect against a general data leak through a single account.
It is crucial that passwords are intricate and contain symbols, capital and lowercase letters, numbers, and other characters. Alternatively, use passwords with the necessary complexity that were generated automatically. You can also set up automatic password expiration to make sure that workers don’t forget to update their passwords. Two-factor authentication is advantageous for sensitive data.
Conclusion
How do the advantages of cloud computing stack up against the security risks? The numerous benefits of working in the cloud far outweigh the few, manageable drawbacks. As cloud computing continues to advance and increase security while providing more and more options for various business models, you have the ability to safeguard your data from potential threats.
So, there’s no reason to be afraid of setting your organization ahead in the cloud with the right technology, sufficient study, and proper research. Furthermore, the companies also try to implement edge computing. You can always get in touch with Jelvix with your request because it has expertise in cloud technologies, the right experts, and successful cases.
FAQ
How to Choose the Right Cloud Computing Service?
Choose a service based on the cloud computing risks and benefits we have outlined in the article. For example, the Jelvix custom software development team has created an app that enables users to set up a completely secure account with possible fingerprint security access. The application is simple to use and secure, allowing users to design their own advanced document management systems. Check out our blog for more information on cloud computing systems.
How Can I Safeguard My Data on the Cloud?
When you back up your data, you will avoid losing data that is crucial to your company’s success. Data encryption would offer an extra degree of protection to your data, safeguarding it from cybercriminals as well as other cloud computing security risks. Ensure to arrange it ahead of time, removing your own personally-identifying information and confidential documents in case of a breach (according to Forbes).
Need a qualified team of developers?
Reach top talent pool to handle end-to-end delivery of your project.