Software and hardware must consistently communicate in a corporation or any work setting to support interactions like meetings, calls, emails, messaging, and various office communications among employees. Businesses require fast and dependable networks for seamless operations and maximum uptime to operate efficiently and effectively. This is where enterprise networking comes in.
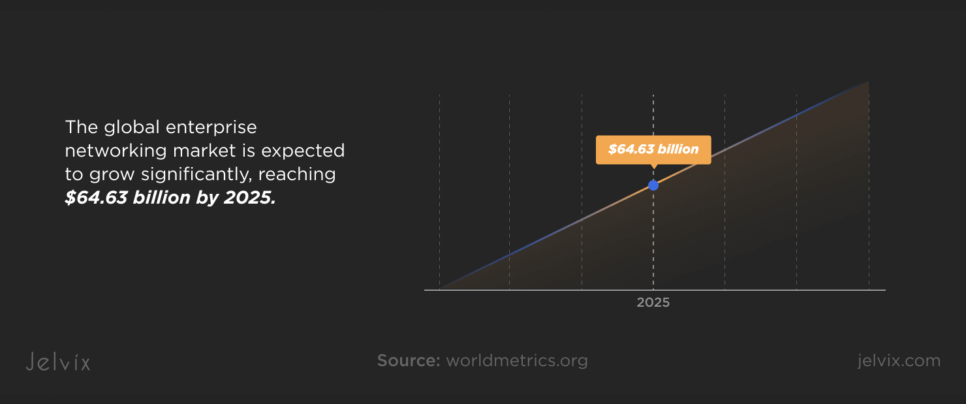
Network infrastructures in 2024 are growing more intricate, driven by multi-cloud adoption and AI-assisted management tools transforming business operations. It is also safe to say that according to industry reports, the global enterprise networking market will grow at a considerable rate and reach $64.63 billion by 2025, which means more scalable and adaptable networks are becoming a “must” for businesses.
In this dynamic environment, enterprises must balance cutting-edge solutions with robust security frameworks. Therefore, in this article, we will explore definitions, the latest trends, challenges, and innovations shaping enterprise networks.
What Is Enterprise Networking?
At its core, an enterprise network is a complex web of interconnected computers designed to meet the needs of large organizations. It links a company’s local area networks (LANs) to broader networks, such as wide area networks (WANs) and cloud infrastructures, forming a cohesive ecosystem. This infrastructure helps users constantly exchange data, work on business applications, and monitor networks, allowing enterprises to run smoothly.
A simple answer to “What is an enterprise network?” would be: it is a hardware and software infrastructure that links computers, servers, and devices. This network allows employees to access shared resources and grants access to internal and external applications.
These networks integrate data centers, branch offices, IoT devices, and cloud services in an enterprise context. Unlike public networks, enterprise networks are closed systems that restrict access to authorized users and devices. They rely on advanced security measures such as virtual private networks (VPNs) and TLS encryption to protect sensitive data from unauthorized access.
Another thing that differentiates enterprise networks from smaller ones (e.g., home LANs) is the scale. While a home network may only connect some devices through a router, enterprise networks link thousands. Sometimes, the scale reaches multiple geographic locations. More extensive networks may even receive autonomous system numbers (ASNs), identifying them as distinct entities on the Internet.
The Impact of Enterprise Networking on Your Business
Keeping operations smooth and well-connected isn’t the only benefit corporations gain from enterprise networking. First and foremost, it improves the user experience by ensuring proactive network optimization, faster incident resolution times, and proper traffic prioritization of critical application data. It also helps maintain security and privacy.
Enterprise network management tools, such as network controllers, give administrators many abilities. Administrators can control who has access and what applications are allowed from which department or user group. They can add new users or functions seamlessly to resources, handling performance management for efficient action.
Enterprise networks protect and enforce security protocols. Features like device identification, profiling, verification, network monitoring, authentication, segmentation, and account management can help businesses limit their exposure to cyber threats.
Next-generation networking and security advances are available using subscription-based licensing on enterprise networks. This enables them to scale with their growing needs as technologies and requirements evolve.
Enterprise networking enables seamless connectivity between users and cloud applications over the numerous public clouds, which are experiencing a tidal wave of new data sets and apps created, deployed, and delivered. In addition, it balances workloads between on-premises and public clouds.
Therefore, an optimized enterprise network is more than just infrastructure. It’s a strategic, many-in-one asset that drives efficiency, security, and innovation. Whether through improved connectivity, enhanced security, or easier management, businesses with well-designed networks are better positioned to thrive in today’s competitive market.
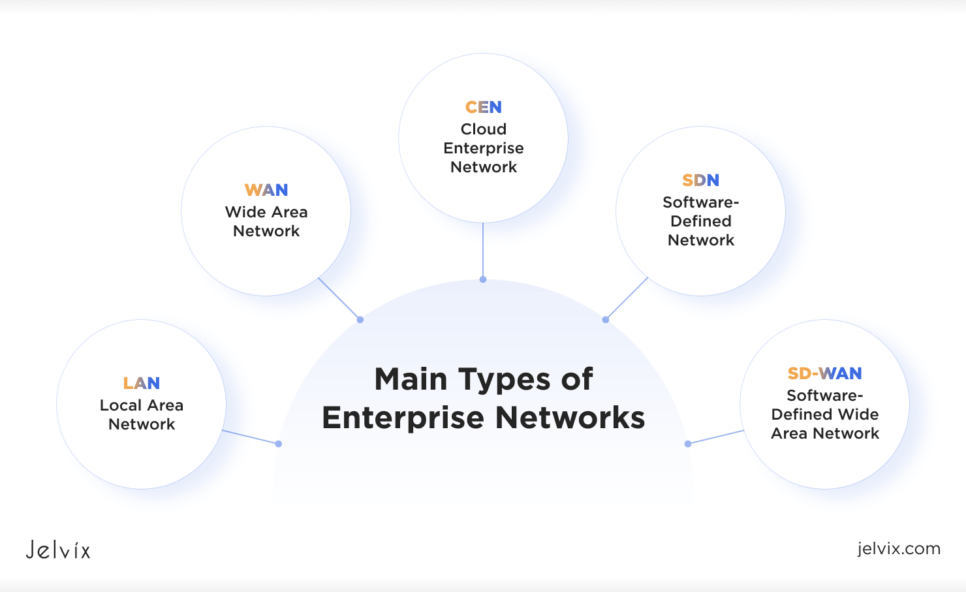
Main Types of Enterprise Networks
The enterprise network creates a secure link between devices to share information safely. It can range from connecting two devices with cables and adapters to wirelessly linking thousands of devices. There are various enterprise networks that exist, and we will outline the most prevalent types below.
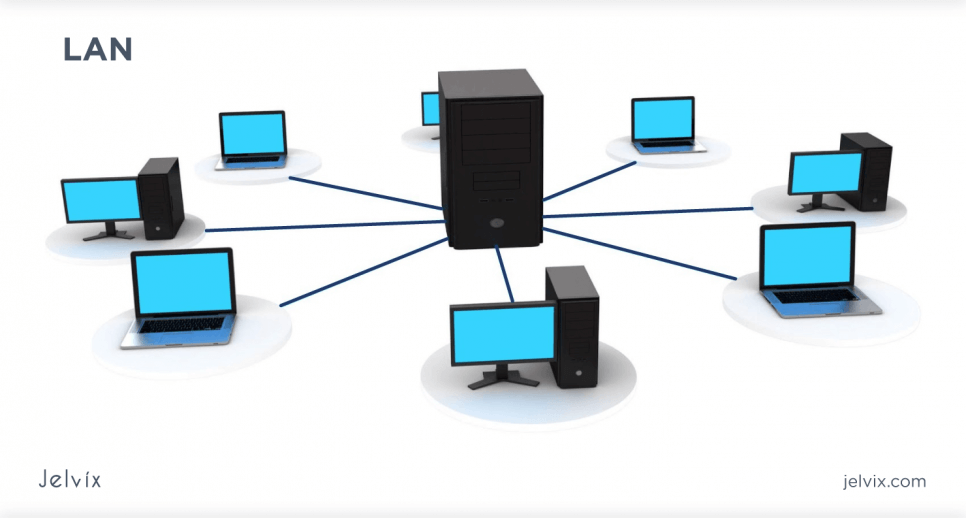
Local Area Network (LAN)
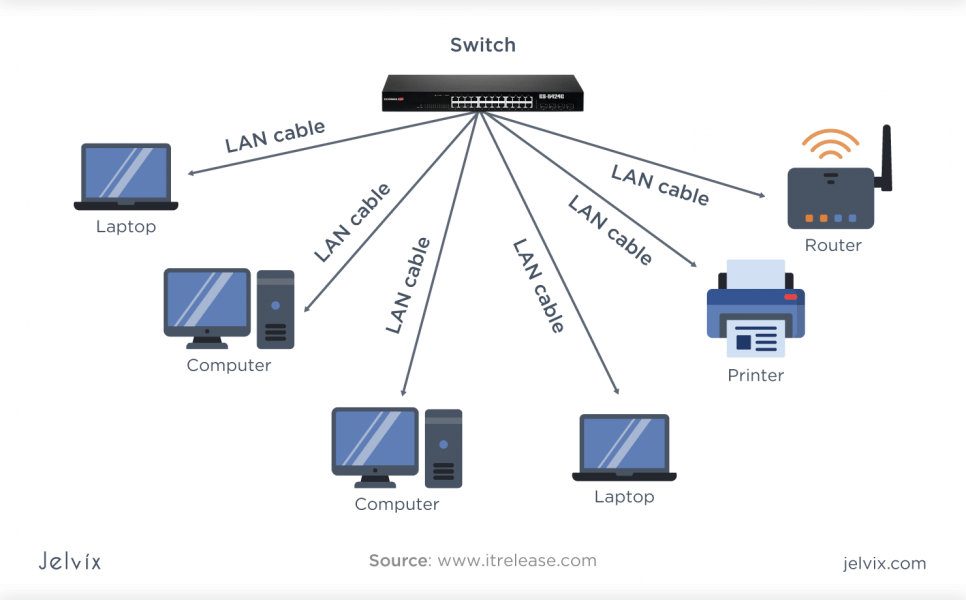
A LAN is a network that interconnects computers within a limited area, such as an office building, college campus, or data center. It is built with affordable hardware (such as Ethernet cables, network adapters, routers, and computers) for a wired connection. These networks ensure rapid and secure connections between internal resources, directly supporting essential operations like file sharing and printing.
Local area networks commonly use wired connections for faster internet speeds, but they can also be fully wireless with central Wi-Fi, known as WLAN (wireless local area network). LAN or WLAN connections are common in residences, personal Wi-Fi setups, work environments, and public networks.
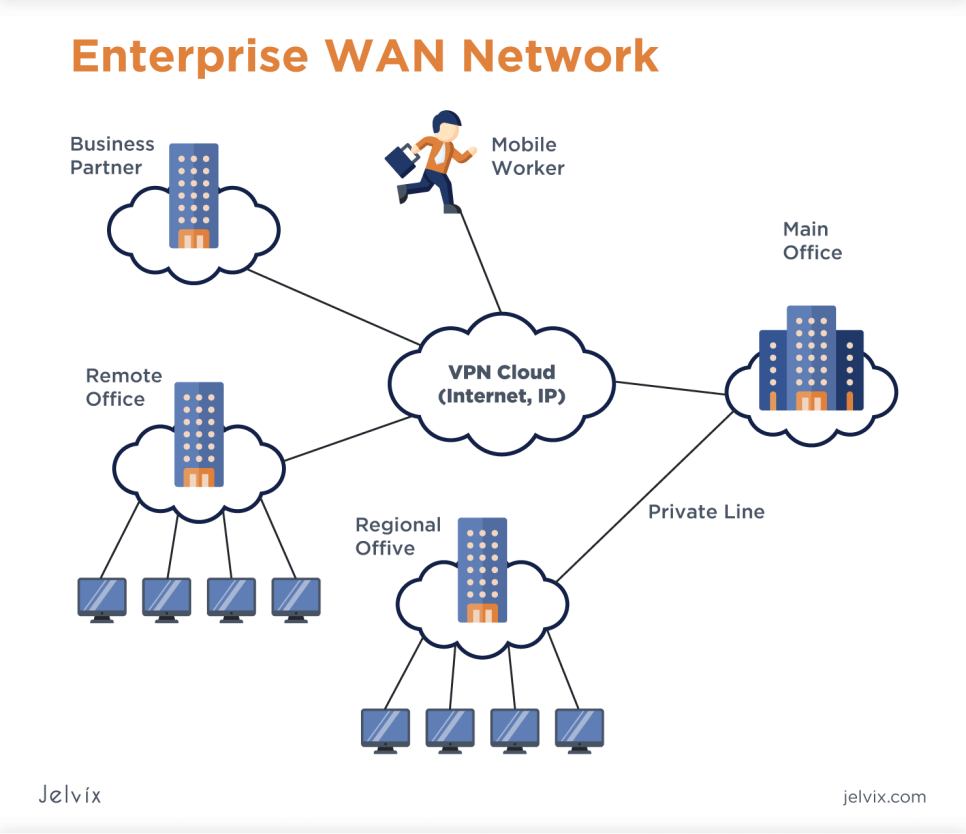
Wide Area Network (WAN)
A WAN connection covers a larger area compared to local area networks. Wide area networks can extend across countries, continents, and the world without being limited to a specific location or geographic area. WAN connections are the most complex and costly computer networks, typically owned by service providers and leased to the public.
Multiple smaller networks, such as LANs and MANs, can be interconnected to create a WAN. Large corporations and global institutions can link their local area networks in separate office buildings and branches using a wide area network.
A developed WAN will enable the exchange of data and information across extensive distances. The Internet is seen as a WAN with no borders. Additional wide-area networks consist of virtual private networks (VPN) and mobile broadband connections, such as the 3G, 4G, and latest 5G networks.
Software-Defined Network (SDN)
SDN is a networking technique that communicates with underlying hardware infrastructure and manages network traffic using application programming interfaces (APIs) or software-based controllers.
This architecture differs from traditional networks, which regulate network traffic using specialized hardware devices (such as switches and routers). SDN can use software to build and manage a virtual network or manage conventional hardware.
Software-defined networking offers a new method of managing data packet routing via a centralized server. At the same time, network virtualization enables enterprises to divide various virtual networks within a single physical network or to link devices on various physical networks to create a single virtual network.
Software-Defined Wide Area Network (SD-WAN)
SD-WAN is a virtual or cloud-based WAN that is configured and managed using software programs. A software-defined wide area network (SD-WAN) is an innovative virtual WAN structure that is operated by software and essentially created by utilizing SDN technologies on standard WAN links.
This allows for improved and safe connections without the requirement for hardware monitoring of outdated computer networks. SD-WAN provides greater flexibility than traditional WAN, better bandwidth utilization, enhanced business efficiency, and reduced IT expenses. It provides improved network connectivity while lowering costs, all without sacrificing security and data privacy.
The adaptability of software-defined WAN is ideal for addressing constantly evolving IT obstacles. It streamlines and simultaneously improves WAN connections, making it easier to integrate and adopt for quickly addressing new challenges and meeting evolving needs.
Cloud Enterprise Network (CEN)
A cloud enterprise network leverages cloud infrastructure to connect users, devices, and resources across both on-premises and cloud environments. Regardless of whether applications are hosted in private or public clouds, they deliver frictionless communication along with critical application access. Modern businesses rely on distributed teams and hybrid applications; this network type provides the flexibility and scalability companies need to manage.
Cloud corporate networks ensure continuous service by optimizing workloads between internal infrastructure and cloud providers (such as AWS, Azure, or Google Cloud). Additionally, they offer redundancy, which helps companies minimize downtime and maintain high availability.
Each type of enterprise network plays a unique role in keeping businesses connected and operational. Organizations typically use a mixture of these networks, such as LANs for internal communication and WANs to connect remote offices. Cloud networking helps to provide infrastructure scaling.
Learn the key steps and strategies to initiate a successful digital transformation, enhancing efficiency, innovation, and competitive advantage.
What Is Enterprise Network Architecture?
Enterprise network architecture is a structured design and layout of a company’s network that ensures seamless communication between all devices, users, and systems. It details how specific components, such as routers, switches, firewalls, etc., connect to facilitate their operations and manage the core business processes, including areas of data storage, VoIP, communication, or distribution of network traffic.
Core Structure and Components
Historically, the enterprise network was focused on centralized data centers. Applications and data resided on-premises, with access managed in corporate offices over LANs. The LAN of each office is connected to the other branches through a WAN, which commonly utilizes MPLS (Multiprotocol Label Switching) paths. This comes together as a hub-and-spoke, with all traffic going in and out through the central data center.
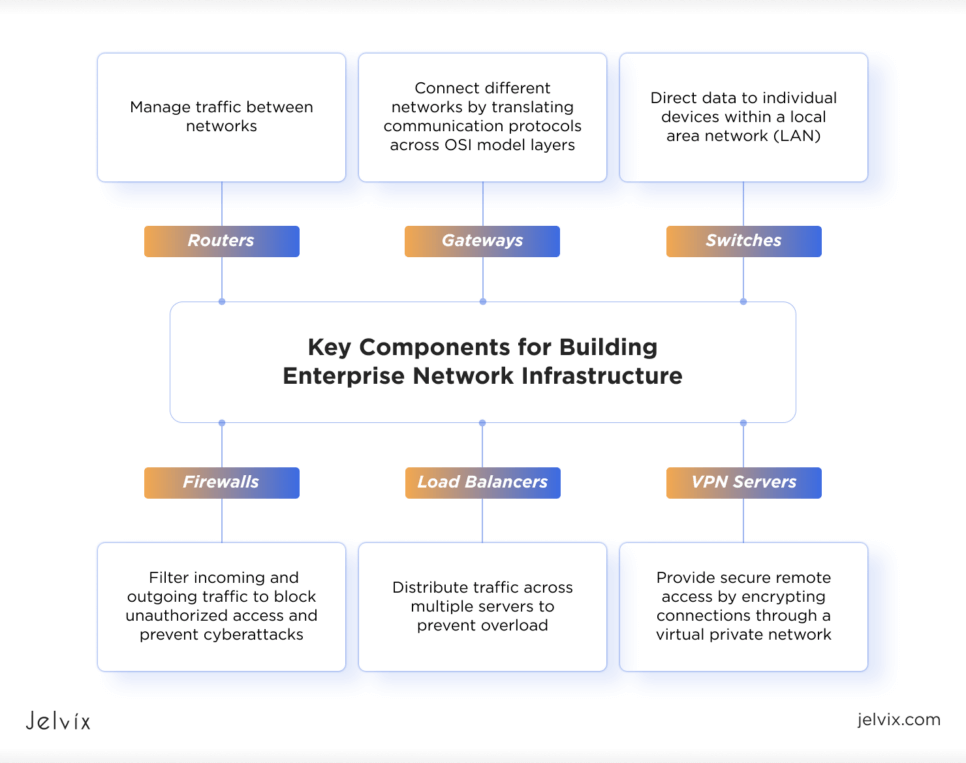
Key components used to build this infrastructure include:
- Routers: Manage traffic between networks.
- Switches: Route data to individual devices within a LAN.
- Gateways: Connect different networks by translating communication protocols across OSI model layers.
- Firewalls: Filter incoming and outgoing traffic to block unauthorized access and prevent cyberattacks.
- Load Balancers: Distribute traffic among multiple servers to prevent any of them from becoming overloaded.
- VPN Servers: Provide secure remote access by encrypting user connections through a virtual private network.
Historically, remote users used to access the enterprise network by connecting to a VPN. It encrypted and routed their data through the VPN server, granting access to the organization’s internal resources.
Modern Enterprise Network Domains
The architecture of an enterprise network today spans several interconnected domains:
- IoT, Branch, and Campus Networks. This includes the domain of IoT devices and internal networks in branch offices or campus facilities, which allow you to communicate across different sites.
- WANs. WANs connect various branch offices, enabling cross-location data exchange and collaboration. These networks and processes are key to expediting global operations.
- Data Centers and Hybrid Clouds. Today, many businesses use hybrid cloud infrastructures that blend on-premises equipment with public and private clouds. This domain ensures scalable storage and access to applications from any location.
- A Virtual Private Cloud (VPC) combines hardware and software solutions to create a secure, customizable network space. It enables businesses to manage cloud-based applications and resources with high flexibility and security. With VPCs, enterprises can control network traffic, define access controls, and allocate resources without compromising privacy.
From facilitating telecommunications systems to conducting real-time data quality analytics, enterprise network architecture underpins critical business operations. A well-designed architecture allows administrators to monitor the performance, regulations, and maintenance of one or more alternative environments.
How Does Enterprise Networking Work?
An enterprise network includes endpoints (computers, phones, IoT devices) connected with networking devices like routers, switches, etc. These hardware components act as intermediaries, ensuring that data flows efficiently and reaches the right destination.
Routers and switches act as traffic controllers to regulate the appropriate paths for data packets based on their destination addresses. They also manage multi-cloud and hybrid communications, allowing data to move back and forth between workloads from on-premises systems to cloud services. When users interact with the shared resource or application, their data is transferred through numerous network devices, which direct this information to the right server or endpoint.
Every device within an enterprise network uses its own operating system and configuration settings. However, to ensure compatibility, these devices must communicate using standardized protocols like TCP/IP or IPX/SPX. Communication protocols define how data is packaged, transmitted, and received, making it possible for diverse devices to exchange information reliably.
Proxy servers are common security appliances used to secure enterprise networks. They serve as intermediaries for request processing between users and external resources. Proxy servers offer additional security by filtering incoming and outgoing traffic, concealing internal IP addresses, and monitoring data flows for potential threats. They are an important component of multi-level security that enables businesses to control access, mitigate theft from outside, and protect sensitive information.
How To Develop an Optimized Enterprise Network
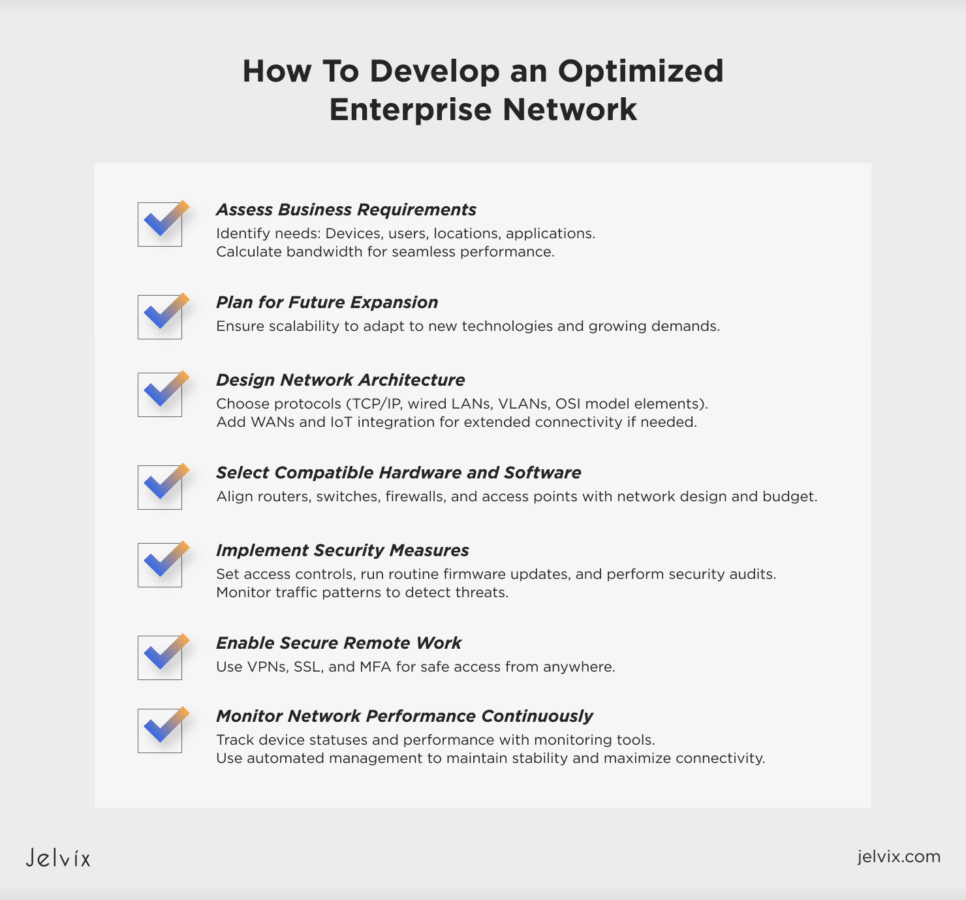
The first step is assessing business requirements. It involves:
- Identifying the organization’s specific needs, including the number of devices, users, locations, and applications required;
- Calculating bandwidth needs to ensure seamless performance.
A plan for future expansion allows the network to scale as demands grow, keeping it adaptable to new technologies and evolving requirements.
The next step is designing network architecture. This includes choosing the right protocols and technologies to support the company behind it. Core elements typically include TCP/IP protocol suites, wired LANs, firewalls, VLANs, and components in the OSI model. Depending on the business model, additional elements such as WANs and IoT integration may be incorporated for extended connectivity.
It’s essential to select compatible hardware and software. Suitable routers, firewalls, switches, and access points align with the network design and budget. Hardware and software must be compatible to avoid performance issues or integration failures.
Implementing robust security measures helps safeguard the network from unauthorized entry and cyber risks. Access control mechanisms manage user permissions, while routine firmware updates and security audits tackle vulnerabilities. Monitoring software can identify unusual traffic patterns, providing extra protection for the system.
Discover expert strategies to scale your IT infrastructure efficiently, ensuring flexibility, performance, and cost-effectiveness as your business grows.
Set up VPNs, SSL protocols, and multi-factor authentication (MFA) to support remote work. These tools ensure employees can securely access internal systems from any location, supporting seamless work-from-home arrangements or mobile operations.
Implementing monitoring tools to track the network’s performance over time is critical. As the number of connected devices rises, stability is maintained through ongoing monitoring. By monitoring device statuses and performance data, automated management solutions offer actionable insights and assist in maintaining network efficiency and maximizing connectivity.
Challenges and Solutions for Enterprise Networks
Enterprise network systems surely solve many problems and help businesses build successful workflows, but they also come with their own set of challenges. Networks get more complex as enterprises scale — with a wider variety of devices, multiple locations, and more clouds to manage. Handling multiple IP addresses, managing hybrid systems, and troubleshooting issues across distributed locations becomes overwhelming, often leading to downtime and inefficiencies.
To ensure scalable infrastructure, simplifying the network infrastructure by minimizing unnecessary components would be beneficial. Businesses can easily automate manual labor with automation tools and software-defined networking (SDN). With SDN, network operators can fully control traffic flows, streamlining operations across hybrid and multi-cloud environments.
Security risks and cyber threats continue to rise. The global average data breach cost has increased 10% from 2023 to today, reaching USD4.88 million. Cyberattacks are a constant threat, especially as IoT devices, cloud platforms, and remote work expand the attack surface. This can lead to:
- disrupted operations;
- exposed sensitive data;
- damaged the company’s reputation.
As a solution, combine network segmentation, firewalls, encryption, and frequent security audits to create a layered security strategy. To reduce risks, cybersecurity recommended practices must be taught to employees. To identify and stop threats in real time, businesses should also deploy network monitoring technologies and multi-factor authentication (MFA).
It is very complex to successfully navigate the ever-changing regulatory landscape, especially in industries where data protection laws are stringent. Non-compliance can lead to serious legal action, fines, and reputational damage.
To ensure compliance, businesses should develop a robust strategy that includes regular audits, compliance assessments, and thorough documentation maintenance. Network systems should be kept up to date to comply with the most current industry-specific regulations. Creating protocols for keeping audit trails and monitoring compliance throughout the network reduces potential legal liabilities.
Another challenge is network management. This can be expensive and complicated, especially when monitoring network performance across different environments. For large enterprises, high-level tools are necessary for maintaining network stability, although they come at an extra cost and require skilled professionals. Smaller companies may struggle with finding affordable solutions.
Reducing infrastructure costs can be helped by using open-source monitoring tools or cloud-based network management platforms. Automated monitoring systems can help track performance metrics, device health, and network traffic in real time, enabling businesses to detect and resolve issues before they escalate. Custom enterprise solutions are also beneficial when designing networks with infrastructure scalability in mind.
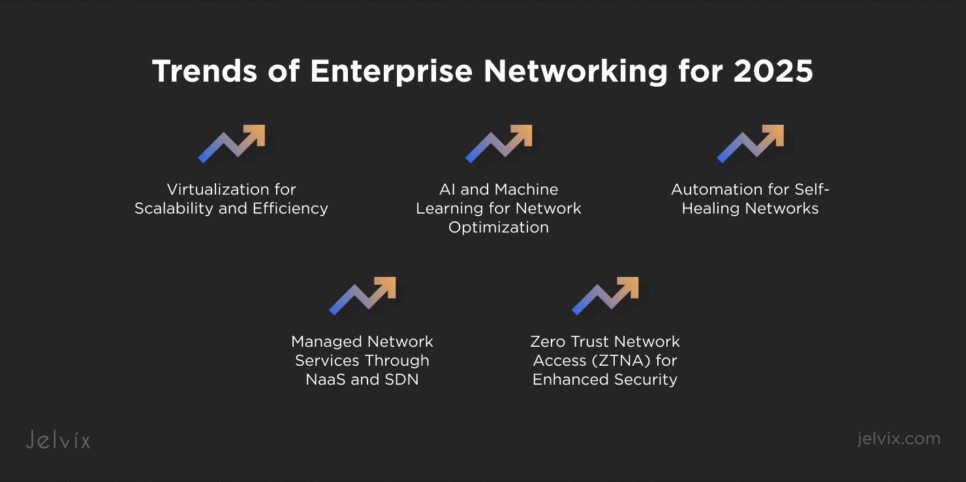
Trends of Enterprise Networking for 2025
Businesses’ networking requirements are always changing. Cloud-based, virtual, and on-premise systems are now all part of modern enterprise networks, which are no longer limited to straightforward configurations. In 2025, enterprise networks will be shaped by the following major trends, which will help companies remain safe, scalable, and flexible.
Virtualization for Scalability and Efficiency
This means enterprises can build a highly elastic network infrastructure that seamlessly scales and relies less on hardware. Using virtualized networks, businesses can do both: handle numerous different types of traffic at once without suffering from poor performance and scale bandwidth up or down dynamically according to demand.
Automation for Self-Healing Networks
By automating routine tasks, enterprises can implement self-healing networks that automatically detect and resolve issues before they escalate. This minimizes the chances of expensive downtime and enables IT teams to direct their attention toward strategic initiatives. For those systems where uptime is important, automation provides continued execution even when surprises come in.
Managed Network Services through NaaS and SDN
NaaS and SDN are becoming popular models for delivering networking solutions on demand. Managed service providers (MSPs) can offer Network-as-a-Service to enterprises, reducing the burden on in-house teams. Meanwhile, SDN enables companies to control their entire network as a unified resource, simplifying management through software-based platforms.
AI and Machine Learning for Network Optimization
Artificial intelligence (AI) and machine learning (ML) are revolutionizing network management by offering sophisticated insights into network security and performance. By continuously detecting threats, these technologies improve security, anticipate and prevent possible problems, and optimize infrastructure for maximum efficiency. Businesses can also make well-informed judgments about network modifications in real time with the help of AI-powered analytics.
Zero Trust Network Access (ZTNA) for Enhanced Security.
Zero Trust Network Access (ZTNA) ensures that every access request is verified at multiple layers of authorization, even from users already inside the network. ZTNA provides an additional safeguard against ransomware attacks and data breaches, making it especially valuable for industries that handle sensitive information, such as healthcare and finance.
Wrapping Up
Building and maintaining a robust enterprise network is essential for modern businesses to remain competitive, secure, and adaptable. From managing network complexity to implementing advanced security measures, enterprise networks require careful planning, reliable hardware and software, and proactive monitoring to ensure seamless operations.
Jelvix provides custom services to help businesses develop and maintain high-end enterprise networks. From smooth cloud integration to successful SD-WAN deployment and from network automation up to security solutions — Jelvix has enormous experience in every area, helping you run your business scenario as quickly as possible. Knowing the evolution of associated technology, Jelvix can ensure that your network is scalable and secure, allowing new technologies to be adopted with confidence for early-movers advantage.
So book a free consultation with Jelvix experts today! Let’s build an enterprise networking solution tailored to your needs.
Need a qualified team of developers?
Reach new business objectives with the dedicated team of professionals.