If you are involved in software development, you probably know what DevOps is. Its methods are becoming more popular in developers’ circles, so no wonder why the majority of huge companies are implementing it in their workflows.
So it shouldn’t surprise you that 63% of DevOps experts and developers say they’ve improved the quality and speed of their software deployments, 55% report improved collaboration, and 38% say they’ve improved code quality. What’s more, Puppet Labs reports a 50% reduction in defects and crashes.
At the same time, over 50% of surveyed companies found the DevOps approach “very difficult.” They all called security as the bottleneck in this strategy. In response to these concerns, SecDevOps was born.
How Did the SecDevOps Movement Begin?
Traditionally, large software companies released new applications every few months or even years. It provided enough time for the code to pass quality assurance and security testing – autonomous specialized teams were responsible for these processes.
However, with the growing use of public clouds, many flows have been automated using new technologies and tools, allowing companies to innovate faster and stay ahead of the competition.
After the emergence of containers and the microservice model, monolithic applications began to break down into smaller, independent parts. This made the way software was developed and deployed more flexible.
Still, most security and compliance monitoring tools did not show such progress. As a result, most of them couldn’t test their code as quickly as a typical DevOps environment required.
Implementing SecDevOps was supposed to fix this issue and fully integrate security testing into the continuous integration (CI) and continuous delivery (CD) pipelines while developing the knowledge and skills needed in the development team for testing and patches to be done internally.
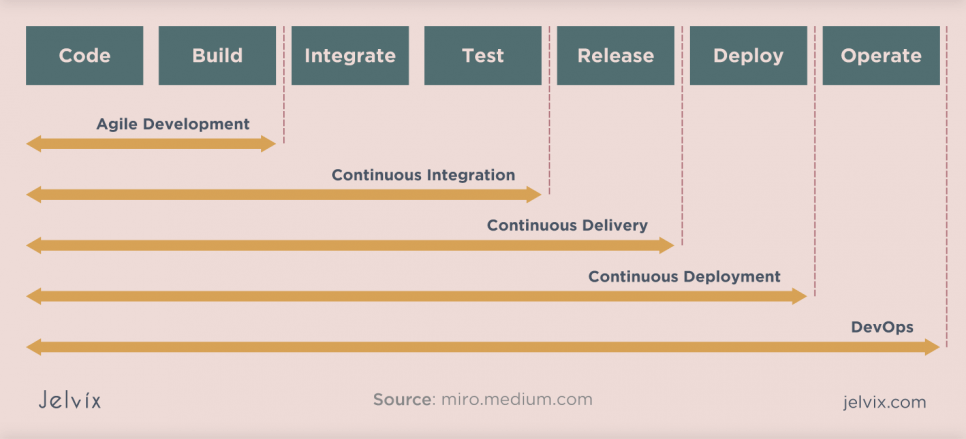
From Agile to DevSecOps
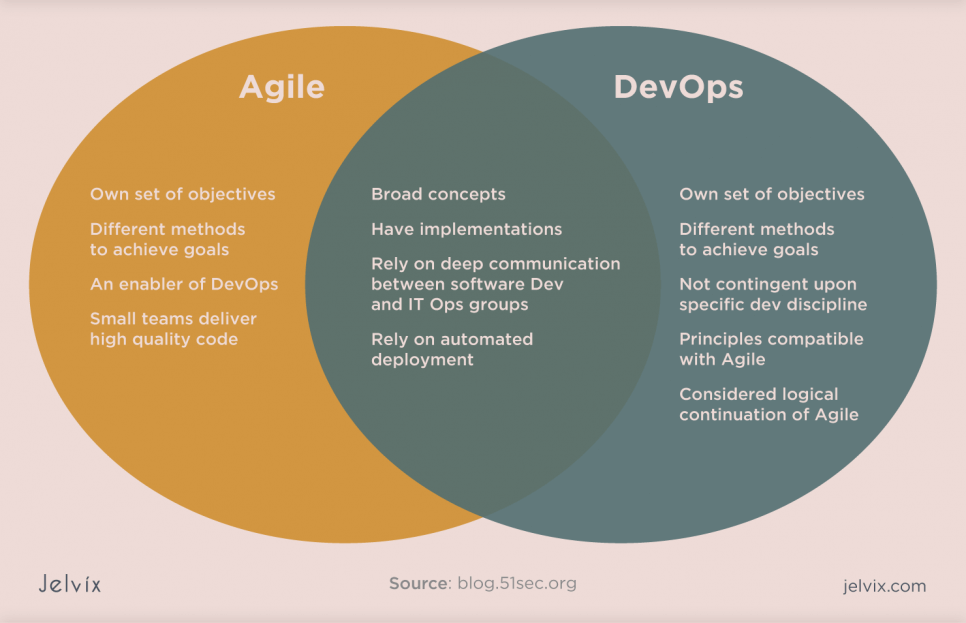
People often ask: what is the difference between DevSecOps and Agile? But we see no point in opposing them to each other. Each approach contains components of the other, so they must coexist for organizations to maximize their business opportunities.
However, it is essential to note that you can implement DevSecOps in any environment – Agile or otherwise.
- The target area for Agile is software development, while the target area for DevOps is creating end-to-end business solutions and fast delivery.
- DevOps is the practice of bringing development and operations teams together, whereas Agile is an iterative approach that centers on collaboration, ongoing feedback and small, rapid releases.
- DevOps requires a relatively large team, while for Agile, a small group will be enough.
- DevOps converges on continuous testing and delivery, while the Agile process focuses on constant change.
- DevOps utilizes the left and right shift principle; on the other hand, Agile uses the left shift principle.
- DevOps focuses more on operational and business readiness, while Agile concentrates on functional and non-functional readiness.
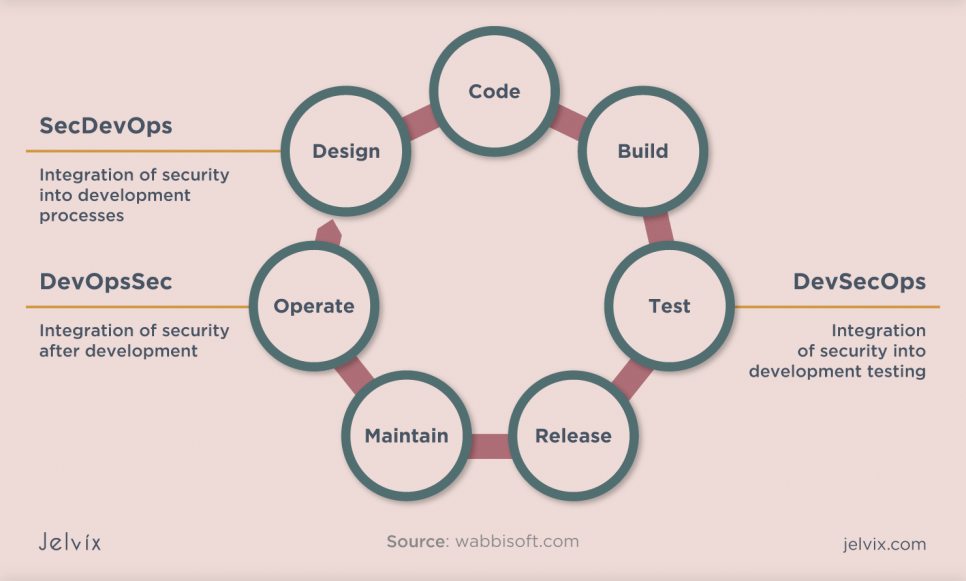
DevSecOps vs. SecDevOps in a Non-literal Sense
Many people think these terms are interchangeable, but they have completely different meanings.
So, what is DevSecOps? The primary focus of the DevSecOps pipeline is to create a seamless and agile software development process. To be effective, all groups collaborate throughout the entire pipeline. However, in most cases, DevSecOps prioritizes development and addresses security issues.
In turn, the SecDevOps pipeline shifts security to the left, removing silos and bottlenecks in the first place. The teams work closely together to ensure the reliability of the applications, and all project participants are responsible for the quality and safety of the final product.
Automation is an essential aspect of the pipeline because it contributes to productivity. The SecDevOps model requires tools that automate as many repetitive tasks as possible.
Besides automation, pipelines require tools that integrate the technology stack and provide a centralized interface. SecDevOps assumes that all DevOps professionals must work with these tools to implement security effectively.
However, we would like to point out that DevSecOps and SecDevOps most often refer to the same idea of embedding security into each stage of the SDLC and taking the same set of benefits into account.
What is SecDevOps?
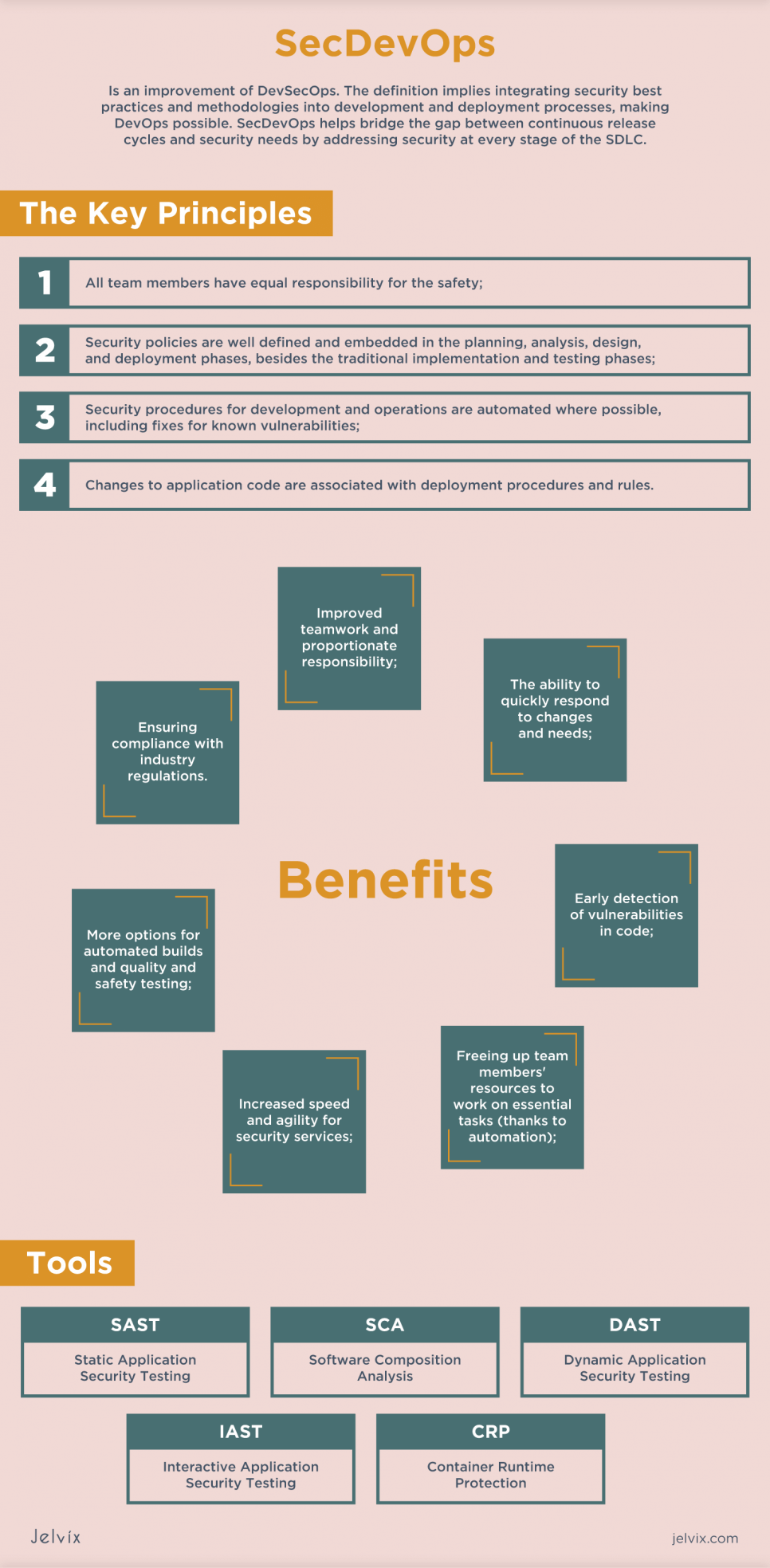
In a nutshell, SecDevOps is an improvement of DevSecOps. The definition implies integrating security best practices and methodologies into development and deployment processes, making DevOps possible. SecDevOps helps bridge the gap between continuous release cycles and security needs by addressing security at every stage of the SDLC.
In addition, the approach is to practice continuous and automated security testing even before the application is released into production. It presents issue tracking to ensure that it detects any defects early. This approach also foresees automation and testing to provide more efficient security tests throughout the SDLC. The key principles of SecDevOps are:
- All team members have equal responsibility for the safety;
- Security policies are well defined and embedded in the planning, analysis, design, and deployment phases, besides the traditional implementation and testing phases;
- Security procedures for development and operations are automated where possible, including fixes for known vulnerabilities;
- Changes to application code are associated with deployment procedures and rules.
SecDevOps comprises two distinct parts:
- Security as Code (SaC) involves building security into the tools in the DevOps pipeline. This means automating manual processes and using static analysis tools that only check the changed parts of the code rather than scanning the entire code base.
- Infrastructure as Code (IaC) defines a set of DevOps tools to configure and update infrastructure components to provide a secure and controlled deployment environment. IaC uses the same coding rules to govern the infrastructure of operations, eliminating inconsistencies and helping to reduce the complexity that often masks security concerns.
Learn more about the fundamental differences between IT Security and IT Compliance.
SecDevOps Advantages for Your Organization
The most important and obvious benefit of the DevSecOps approach is the increased overall security. From a business perspective, the safer a product is, the easier it is to sell it. You can identify vulnerabilities very early in your pipeline, making it much easier to fix them. And continuous monitoring enhances your threat detection capabilities.
SecDevOps defines coding standards, static and dynamic analysis guidelines, testing guidelines, rules to avoid lousy encryption, insecure APIs, etc. It also lists criteria that require manual intervention from the security team (e.g., changes in authentication or the authorization model).
Since security is part of the development process, the SecDevOps team becomes more experienced, ensuring minimal security vulnerabilities at the end of the pipeline. But if any vulnerability persists, the process can quickly be investigated, updated, and improved.
Root cause analysis also helps teams make improvements to security policies and recommendations. In other words, they can improve the result after each cycle. Iterative enhancements additionally provide less destructive escalation later in the cycle.
Some of the more notable benefits of SecDevOps are:
- Improved teamwork and proportionate responsibility;
- The ability to quickly respond to changes and needs;
- Early detection of vulnerabilities in code;
- Freeing up team members’ resources to work on essential tasks (thanks to automation);
- Increased speed and agility for security services;
- More options for automated builds and quality and safety testing;
- Ensuring compliance with industry regulations.
Standard SecDevOps Workflow
Since developers work in source control, they can track any changes in software development projects. They easily split their tasks using branches, collaborating on the code.
So, first, the code is created, and the changes in the system are recorded. The static code is then analyzed to identify security flaws or bugs. The standard SecDevOps workflow then proceeds as follows.
IaC tools create an environment to deploy an application and apply security configurations to the system. Next, a test automation suite is executed for the newly deployed application, including back-end, integration, API, security, and user interface tests.
The team then automatically tests the deployed app in a test environment. The next step is to deploy the app to the production environment and continuously monitor the production environment for active security threats.
DevSecOps Tools
Security and compliance toolkits are available to address various aspects of the SDLC. That includes software composition analysis (SCA), static code analysis (SAST), and all kinds of approaches to testing code for vulnerabilities (IAST and DAST).
In addition, there are tools designed to monitor and protect binaries in production environments from attacks that exploit your code or vulnerabilities in your environment. Ideally, teams should strive to use these tools for complete SDLC security.
SAST
These tools help identify vulnerabilities in an already developed code. Developers can use them as an automated part of the development process and detect and remediate potential vulnerabilities early in the DevOps cycle. Examples of static analysis tools are SonarQube and Veracode.
SCA
Software composition analysis includes managing and monitoring license compliance and security vulnerabilities in open source components.
Enhanced SCA tools offer capabilities to prevent binary downloads and build failures, enforce policies, and send notifications to other systems. The vulnerabilities found by the SCA tool are easier to fix as the developer community fixes 97%, and you just need to make changes or download the latest version.
DAST and IAST
Dynamic and Interactive Application Security Testing tools test open interfaces of a running application for vulnerabilities and flaws. While DAST views an application as a black box, IAST uses a combination of DAST and SAST to improve the accuracy of application security testing. Examples of IAST tools include Synopsys, Contrast Security, and Checkmarx.
Container Runtime Protection Tools
These tools keep track of containers in their runtime and provide a variety of capabilities, including anomaly detection based on behavioral analytics, firewalls at different levels, and much more. Examples of runtime protections include NeuVector, Twistlock, and Rezilion.
What is the Role of SecDevOps in Cloud Security?
Public cloud migration gives organizations access to innovative tools and capabilities offered by CSPs such as containers, microservices, DevOps functionality, CI/CD, and enhanced serverless architecture. This has helped speed product development, including design, assembly, and product release, helping companies significantly reduce time to market.
The cloud can improve platform integrity through automated, built-in security processes and tools. But don’t place the responsibility for security solely with cloud service providers.
Safety should be built at every level using SecDevOps best practices and patterns. In doing so, priority should be given to ensuring authentication and authorization, protecting confidentiality, maintaining data integrity, and ensuring availability when needed.
It also requires significant changes in the workflow. For example, clouds, services, and applications can be quickly updated or changed with the click of a button, and traditional security solutions will lag behind these rapid deployments.
You can use the DevSecOps approach to adjust processes and thinking towards more dynamic, collaborative, and iterative operations, with an ongoing focus on security at every stage.
Implementing security through design can be a good solution to build security into all processes and products early. This will provide more robust and consistent protection, rather than a system that relies on adding security patches as an afterthought.
SecDevOps Best Practices
The SecDevOps approach in software development reflects the company’s maturity. If you are developing a product within a startup, you most often do not need such a process since it requires a lot of human and material resources. But for a large company with financial and GR risks, many security measures are more than appropriate and can solve many problems before they appear in the production environment.
The company must be mature enough to add “Sec” to the “DevOps” acronym. You are not required to be strict about security during the development process. But keep in mind that we are talking about companies that do not need to comply with the requirements of external regulators. For the rest, security is dictated by the specifics of the business.
While there is probably no one-size-fits-all approach, there are a few best practices that any company looking to implement SecDevOps can adopt.
Practice Secure Development
SecDevOps requires prioritization of security, often encouraging developers to adopt secure programming techniques. However, this does not mean developers should urgently learn advanced security tools or become security experts. You can integrate learning into processes so that developers learn and apply security practices at the level necessary for their day-to-day responsibilities.
Red and black deployments can also mitigate risks in a production environment that supports two identical production environments, but with only one running. That allows you to test a new version of your code in a production infrastructure without affecting transactions, sessions, or user interaction.
Determine Security Policies
These policies can include encoding best practices, encryption rules, and testing guidelines when using DAST, SAST, or SCA. Clarity better understands the underlying challenges and constraints and improves application security.
In addition, developers, testers, and other team members must share responsibility for security. This enhances communication between team members, improves security design patterns, and makes security response strategies more dynamic.
Use Version Control for Everything
All application software, patterns, diagrams, and scripts in a DevOps environment should use effective versioning tools and techniques. Version control has many security benefits and allows commands to:
- Investigate and identify the introduction of vulnerabilities or malicious components into the development pipeline.
- Track security incidents down to a specific build or feature.
- Maintain an audit trail of development movements to comply with regulatory requirements.
Automate Repetitive Tasks
Most mature DevSecOps programs use automation early and often. For example, automating security checks helps speed up the development process and improve developer productivity by making it easier to identify potential vulnerabilities in your code. That is especially true for large organizations where developers run different code versions multiple times a day.
Apply Threat Modeling to Identify Gaps
Teams that approach security from an attacker’s perspective are better at identifying weaknesses in their code. This is where DUST comes in. Scanners can be quickly and easily integrated into the development pipeline to add another layer of protection to your applications.
Invest in the SecDevOps Tools
If you’re unsure how to modernize your approach to application security, consider the right DevSecOps tools to enable your team to automate security and merge critical data in those crucial early stages of development where the stakes are highest.
SecDevOps Issues and Ways to Solve Them
Here are some challenges that organizations are adopting SecDevOps face and how to solve them.
Challenge 1: Lack of security talent. This is perhaps the most crucial aspect of prioritizing security. Most times, organizations cannot find as many security experts as needed.
Solution: SecDevOps urges DevOps engineers to take responsibility for protecting their code and IT operations to protect infrastructure. SecDevOps offers tools and techniques to help developers and operations teams perform security analyses, detect security issues, and improve how you program and manage software.
Challenge 2: Resistance to change. Individual team members may not like the drastic change opposed to the way they traditionally used to follow.
Solution: Involve these people in developing innovative solutions; developers can develop automated solutions to help solve security problems without affecting the development speed.
Challenge 3: Security is ignored in the name of continuous development and deployment.
Solution: Create automated security checkpoints to ensure quality targets are met and stop the conveyor if the number of security errors exceeds the target.
Challenge 4: Lack of coordination between the information security team and the developers.
Solution: Integrate bug tracking tools your team uses with security tools so developers can see security bugs as routine tasks.
Challenge 5: Complex tool integration. Most of the DevOps toolkits come from various vendors, and adding security tools makes the task even more difficult.
Solution: Finding one tool that can solve your security problems will make life easier for developers at the individual level and the entire organization.
How to Implement SecDevOps
Now we will list some of the basic steps in any DevSecOps implementation. Remember that your roadmap can include some special additional steps, depending on the complexity and the size of the project.
Planning and Development
The road to SecDevOps starts with planning. However, remember that the plan must be strategic and concise for a successful implementation. Professionals should also establish acceptance testing criteria, user design, and threat models. Simple performance-based descriptions will not suffice.
The next step is development, and the teams should start by assessing the maturity of their existing practices. It is a good idea to gather resources from multiple sources to provide guidance. Creating a code review system can also come in handy, as it promotes consistency, which is one aspect of DevSecOps.
Building and Testing
Then comes the build, where the automated build tools come into play. These tools combine the source code into machine code using an assembly script. Build automation tools are packed with powerful features. Apart from an extensive library of plugins, they offer several user interfaces. Some can also automatically detect any vulnerable libraries and replace them with new ones.
The next step is testing, in which a robust test automation framework injects rigorous testing practices into the pipeline.
Deployment and Operation
Deployments are performed using IaC tools because they automate and speed up software delivery.
Operations are also crucial, and periodic maintenance is a regular feature of operations teams. To prevent human error from occurring, DevSecOps can use IaC tools to quickly and efficiently protect the organization’s infrastructure.
Monitoring and Scaling
Powerful continuous monitoring tools are another vital part of the process. They ensure that your security systems are working correctly.
Scaling is also a necessity. With virtualization, organizations no longer need to spend resources maintaining large data centers. Instead, they can scale the IT infrastructure to manage any threats.
Final Words
The technical and commercial benefits that organizations derive from implementing SecDevOps are significant. With security as the foundation from the SecDevOps perspective, application development and other processes become safer and more efficient.
Innovative companies like Google or Netflix have already made security a necessary part of their DevOps culture. And we at Jelvix also use SecDevOps principles in application development to create the best product for our clients. Contact us if you want to work smarter, not longer.
Need a high-quality professional?
Use our talent pool to fill the expertise gap in your software development.